Despite the advances in cybersecurity, ransomware continues to be a threat to businesses of all sizes. Versatile and hard to prevent, ransomware attacks are a lucrative criminal activity that can cost a company anywhere between a few thousand to millions of dollars.
Read on to learn about the most dangerous examples of ransomware and see why businesses invest heavily in preventing these types of attacks.
What is Ransomware?
Ransomware is a type of software that blocks access to a system or files until the victim pays a ransom. Most attacks make data inaccessible through encryption, but some programs prevent users from booting up their devices.
Ransomware typically infects a system in one of the following ways:
- A malicious attachment or link in a phishing email.
- A drive-by download from an infected website.
- An infected piece of hardware.
- A worm that exploits a system vulnerability.
Here is how an average ransomware attack works:
- A user receives a phishing email and makes the mistake of clicking on a malicious link.
- Ransomware silently installs on the system and locates the target data.
- The program encrypts data in the background.
- Once encryption is complete, the victim gets a message from attackers demanding a ransom in exchange for the decryption key.
Hackers typically demand payments in Bitcoins or similar cryptocurrencies. The ransom always has a deadline. If the victim decides to break the deadline, attackers either increase the price or delete the decryption key.
Giving money to attackers is not always the end of a ransomware attack. Some programs also infect other devices on the network, enabling further attacks. Other examples of ransomware also infect victims with malware, such as Trojans that steal login credentials.
Our article about ransomware statistics shows the real danger of these malicious programs.
Ransomware Types
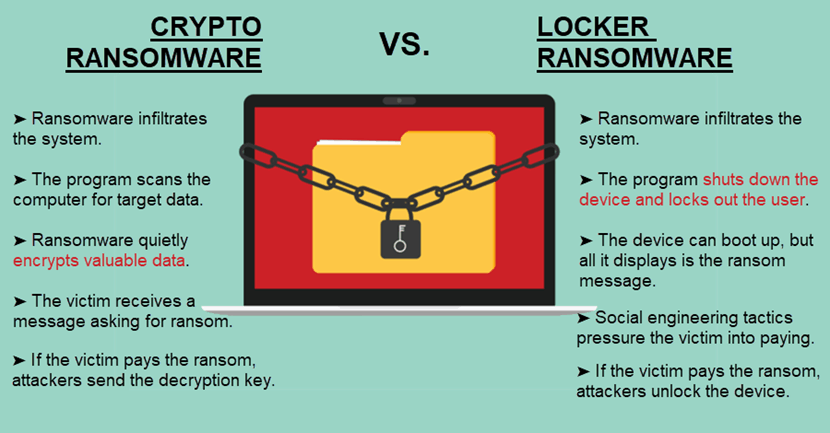
Crypto Ransomware
Crypto ransomware attacks (or data lockers) encrypt files on a computer to prevent the victim from accessing data. The easiest way to restore data is to use a decryption key, which is what attackers offer in exchange for a ransom.
Crypto ransomware typically does not encrypt all data on a device. Instead, the program silently scans the computer for valuable data and encrypts only those files. Typical targets for a crypto attack are financial information, work projects, and sensitive business files.
This type of ransomware does not lock the computer. Victims can continue to use their devices even if they refuse to pay the ransom.
Locker Ransomware
Locker ransomware attacks lock down the entire computer instead of encrypting specific files. Attackers then promise to unlock the device if the victim pays the ransom.
A locker attack typically allows the user to boot up the device. However, the device has limited access and enables the victim to only interact with the attacker.
Attackers behind locker ransomware often use social engineering to pressure the victim into paying the ransom. Imitating tax authorities or law enforcement agencies is a common tactic.
Use sound backup strategies to protect your business both from crypto and locker ransomware attacks.
Ransomware Examples
We’ve created a history of ransomware infographic, which is available for download. Scroll down for additional details regarding each ransomware attack.
1. Reveton (or Police Trojan)
Reveton ransomware began to appear at the end of 2012. Hackers spread Reveton via three tactics:
- Malware packages (such as BlackHole or the Cool Exploit Kit) on insecure websites.
- Spam email campaigns.
- Phishing emails.
Once inside the computer, Reveton scans the device for outdated or exploitable plugins. If the system has a weakness, the program locks the device and prevents the user from accessing the computer.
Reveton relies on social engineering to pressure victims into paying the ransom as attackers often pose as the FBI or a local police force. The ransom message typically says that the user was involved in illegal activity and orders the victim to pay a fine.
Officials arrested the original creator of Reveton in 2013, but different variations of the program are still active. The latest versions of the ransomware install password-stealing malware that stays within the system after the victim pays the ransom.
2. CryptoLocker
The first report of CryptoLocker happened in September 2013. This Trojan targeted devices running Microsoft Windows and spread via infected email attachments and a Gameover ZeuS botnet.
Once activated, CryptoLocker encrypted files on local and mounted drives with RSA public-key cryptography. CryptoLocker was the first ransomware to encrypt data with a different symmetric key for each file. The program was able to encrypt 70 file formats.
CryptoLocker authors successfully extorted around $3 million in nine months. In May 2014, the U.S. Department of Justice disabled the Gameover ZeuS botnet. Operatives also discovered CryptoLocker’s private keys database, which enabled victims to recover lost data with a simple online tool.
3. CryptoWall
CryptoWall first appeared in early 2014. This ransomware spreads via phishing emails, exploit kits, and malicious ads. Upon installation, the program:
- Encrypts data.
- Scrambles file names to confuse the victim.
- Deletes system restore points.
Command-and-control server stores decryption keys, so local decryption is impossible. A notable feature of CryptoWall is that the attackers always offer to decrypt one file for free.
The typical ransom is $700 in Bitcoins, a fee that doubles after a week if the victim does not comply with the request.
4. TorrentLocker
TorrentLocker is a ransomware Trojan that started to appear in 2014. TorrentLocker primarily spread through spam email campaigns. Clicking on the attachment in a corrupt email has two consequences:
- The file installs TorrentLocker on the device.
- Ransomware collects local email contacts and sends further spam emails.
Once the infection starts, TorrentLocker scans the system for programs and files before hiding the contents via AES encryption. The program also deletes Windows volume shadow copies to prevent system restoration. The ransom is typically around $500 worth of Bitcoin, and the victim has three days to pay.
Protect against TorrentLocker and similar ransomware by implementing email security best practices.
5. TeslaCrypt
TeslaCrypt was a ransomware Trojan released in February 2015 that targeted gamers using Windows computers. This program spread through an Angler Adobe Flash exploit.
Once inside the system, TeslaCrypt searched for data files and encrypted them with AES encryption. TeslaCrypt targeted 185 data types in 40 different video games, most notably World of Warcraft and Minecraft. Ransomware encrypted save data, player profiles, custom maps, and game mods.
To decrypt the files, the victim had to pay a ransom of $500 in Bitcoin. Later versions of TeslaCrypt also encrypted Word, PDF, JPEG, and other file extensions.
In May 2016, TeslaCrypt authors shut down the ransomware by releasing the master decryption key. Later, ESET developed a free decryption tool with which victims could recover encrypted data.
6. SamSam (a.k.a. Samas or SamsamCrypt)
SamSam began appearing in late 2015. This ransomware does not rely on any form of social engineering. Instead, SamSam spreads by exploiting system vulnerabilities in JBoss host servers.
Once inside the system, attackers gain admin rights and run an executable file that encrypts data. The victim does not need to open an attachment or infected application.
Over time, SamSam evolved and started to exploit vulnerabilities in:
- Remote desktop protocols (RDP).
- Java-based web servers.
- File transfer protocol (FTP) servers.
SamSam extorted over $6 million and caused more than $30 million in damages. Notable victims of this ransomware include:
- The town of Farmington in New Mexico.
- Davidson County in North Carolina.
- The Colorado Department of Transportation.
- The infrastructure of Atlanta.
The last public reports of SamSam were in mid to late 2018. However, no arrests happened, nor was there ever an official announcement about the program’s cancellation.
7. Locky
The first Locky attacks happened in February 2016 when hackers sent about half a million corrupt emails to random addresses.
Locky spreads by phishing emails with malicious attachments. A typical strategy is to send fake invoices with an infected Microsoft Word document containing malicious macros.
If the victim enables Office macros within the corrupt document, a binary file downloads a Trojan that encrypts all files with a particular extension. Locky generates decryption keys on the server-side, making manual decryption impossible.
Locky can encrypt over 160 file types. The program’s focus is to target file types common in development, engineering, and QA teams. After encryption, the victim must download Tor and visit a Dark Web website for more information. A typical ransom ranges between 0.5 and 1 Bitcoin.
A later version of Locky started to use a JavaScript attachment that automatically runs if the user opens the file.
8. Cerber
Cerber emerged in February 2016 and was a Ransomware-as-a-Service (RaaS) program. Third parties could use Cerber to attack users and, in return, pay the owners an affiliate fee.
Cerber targeted cloud-based Office 365 users with phishing campaigns. Typically, victims received an email with an Office document. If the victim opened the file, the ransomware quietly encrypted data in the background. The victim then found a ransom note in an encrypted folder or as a desktop background.
Here are some numbers that place Cerber into perspective:
- In July 2016, Cerber infected more than 150,000 victims via 161 campaigns.
- Attackers stole around $2.3 million in 2016.
- At its peak in early 2017, Cerber was the cause of 26% of all ransomware attacks.
There were no reports of Cerber attacks in 2018. Attackers moved on to more advanced ransomware, such as GandCrab and SamSam.
9. Petya
Petya is a program that first hit in March 2016. Instead of encrypting files, Petya encrypts the entire hard drive. Petya primarily spreads through HR departments of mid-to-large companies. Attackers typically send fake job applications with infected PDF files or Dropbox links.
An attack starts with an infection of the computer’s master boot record (MBR). Petya then overwrites the Windows bootloader and restarts the system. Upon startup, the payload encrypts the Master File Table of the NTFS file system. The victim then sees a ransom note asking for payment in Bitcoins.
Organizations targeted by ransomware can ensure business continuity and data availability with Disaster Recovery as a Service.
Attackers typically combine Petya with Mischa, a secondary program that activates if Petya fails to install. Mischa encrypts user documents and executable files.
As companies got better at preventing Petya attacks, the program evolved into more sophisticated versions called NotPetya and GoldenEye.
10. KeRanger (a.k.a. OSX.KeRanger.A)
KeRanger appeared in March 2016 and was the first ransomware to infect Mac devices running OS X. KeRanger spread through the setup file of Transmission, an open-source BitTorrent client.
Once a victim downloads the infected installer, KeRanger silently installs on the system. After three days, KeRanger encrypts about 300 different file types across the Users and Volumes folders. The program then downloads a text file demanding the victim to pay one Bitcoin.
Like CryptoWall, KeRanger attackers often offer to decrypt one file for free. Authors also claim to have a help desk ticketing system for victim’s questions.
11. Jigsaw
Jigsaw first appeared in April 2016. This ransomware gradually deletes files each hour the victim refuses to pay the ransom. The initial name for Jigsaw was BitcoinBlackmailer, but the name changed after attackers started to use imagery from the Saw film franchise.
Jigsaw spreads through a malicious attachment in spam emails. Once activated, the program encrypts all user files and the MBR (master boot record). A popup screen then asks for a ransom and informs that the victim has an hour to pay, or the program deletes a random file. Jigsaw continues to delete data for up to 72 hours, after which the program permanently deletes all encrypted files.
Jigsaw informs the victim that any attempt to restart the computer or terminate the process instantly deletes 1,000 random files. However, Jigsaw can be reverse engineered to remove the encryption due to the program’s use of the .NET Framework.
The latest versions of Jigsaw also threaten to expose personally identifiable information (PII), putting additional pressure on the victim to pay the ransom.
12. Dharma (a.k.a. CrySIS)
Dharma ransomware first appeared in 2016 but became a hot topic in mid-2019. Dharma targets Windows systems only. This ransomware has three distribution methods:
- Spam emails: Victims receive an email containing an infected attachment with double file extensions. These attachments appear as non-executable under default Windows settings.
- Corrupt setup files: The Dharma program poses as a setup file for legitimate software.
- RDP vulnerabilities: Attackers target a weakness in the Remote Desktop Protocol. The process requires brute-forcing the victim’s Windows RDP.
Once inside the system, Dharma encrypts all file types. The program also deletes all Windows Restore Points.
13. ZCryptor
ZCryptor is a 2016 ransomware worm that encrypts files and self-spreads to other devices in the network.
ZCryptor infects the initial victim by imitating a setup file of an ordinary program or a Microsoft Office file. Once within the network, the worm infects external and flash drives to distribute itself to other computers in the network.
Once the attack spreads to enough devices, ZCryptor encrypts the files and asks for a ransom. The initial ransom starts at 1.2 Bitcoin but grows to 5 Bitcoins if the victim does not pay after four days.
ZCryptor can encrypt 80 different file formats. Encrypted data has a .zcrypt extension.
14. WannaCry
The first WannaCry attack occurred in May 2017. By the end of the year, WannaCry spread across 150 countries and infected around 300,000 computers.
This ransomware worm targeted computers with outdated versions of Microsoft Windows, exploiting the EternalBlue vulnerability in the SMB protocol. Once inside the system, WannaCry locked out users and demanded a payment. Ransoms ranged from $300 to $600 in Bitcoins.
Other names for WannaCry are WannaCrypt, WCry, Wana Decrypt0r 2.0, WannaCrypt0r 2.0, and Wanna Decryptor.
Security experts quickly found a kill switch domain that ended WannaCry. WannaCry was still a criminal success, causing over $4 billion in losses worldwide.
15. Bad Rabbit
Bad Rabbit started to spread via drive-by attacks in 2017. These attacks happen when hackers exploit an insecure website to set a ransomware trap. When a user downloads any usual file, the website also sends the ransomware and infects the device.
Bad Rabbit shares many similarities with WannaCry and Petya. The program encrypts the victim’s file tables and asks for a Bitcoin payment to provide a decryption key.
Bad Rabbit installed through a false Adobe Flash update. While the bogus update enabled Bad Rabbit to spread quickly, this tactic allowed security experts to develop a simple prevention method in October 2017. While short-lived, Bad Rabbit managed to infect several high-level targets, such as Interfax and Ukraine’s Ministry of Infrastructure.
16. GandCrab
The first GandCrab attack happened in January 2018. This ransomware targeted users of adult content websites. GandCrab hacked the victim’s webcam and threatened to release embarrassing footage unless the target paid a ransom.
GandCrab only targeted Microsoft Windows systems. All payments were in the form of a cryptocurrency called Dash, and ransoms were anywhere between $600 to $600,000.
GandCrab was one of the most active ransomware threats in 2018. Security providers and the police worked together to develop a decryption tool to rescue the victim’s data. As a result, the team behind GandCrab announced that they decided to retire the ransomware.
17. Ryuk
Ryuk ransomware began to spread in August 2018. A typical attack encrypts files and network drives before disabling the Windows System Restore option.
The team behind Ryuk is WIZARD SPIDER, a group with a reputation for targeting large enterprises and asking for high ransoms. This Russia-based team stole roughly $3.7 million off 52 transactions thanks to Ryuk.
A Ryuk infection starts with a spear-phishing email and a geo-based download function. Once Ryuk enters the network, a ransom file RyukReadMe.txt demands payment in Bitcoins. The ransom demand depends on the size of the target.
18. Phobos
Phobos first appeared at the start of 2019. This ransomware shares many similarities with Dharma, so the two programs likely have the same author.
Phobos relies on weak Remote Desktop (RDP) connections to infiltrate a network. Hacking RDP servers is a cheap process, allowing the attackers behind Phobos to charge less than other ransomware targeting businesses. The average ransom demand from a Phobos attack is $18,755.
19. Netwalker
Cybercrime group Circus Spider created Netwalker in 2019. What sets Netwalker apart is that attackers always leak a sample of the stolen data before contacting the victim. If the company decides to ignore the ransom request, the rest of the data goes to the Dark Web.
In March 2020, Circus Spider started offering Netwalker on a RaaS basis. The shift to RaaS allowed attackers to target more organizations and increase the size of their ransoms.
20. Sodinoki
Sodinoki first appeared in April 2019. Sodinoki (also known as Sodin and REvil) targets mostly American and European companies.
This ransomware gains access via brute-force attacks, server exploits, or phishing emails. After bypassing antivirus software, Sodinokibi downloads a JavaScript .zip file and encrypts data while moving through the network.
Attackers behind Sodinokibi put pressure on victims by doubling the ransom every few days. This ransomware also reinstalls if the original .zip file remains within the system.
21. Maze
The first known attack of Maze ransomware was in May 2019. The initial infection plan relied on spam emails and exploit kits, but now attackers use various tactics and techniques. Hackers often hire an actor to analyze the victim’s revenue and weaknesses.
Once Maze breaches the network, the program moves laterally through the system and deploys file encryption across all drives. Maze encrypts data using the ChaCha20 and RSA algorithms.
Before encryption, Maze exfiltrates data. If the victim decides to ignore the ransom request, hackers threaten to sell or release the data and cause a GDPR problem.
In November 2020, the Maze team announced that the ransomware is no longer active. The news appeared on the Maze website on the Dark Web.
22. Snake
Snake, also known as Ekans, first appeared in January 2020. Unlike other ransomware targeting enterprises, Snake spreads through industrial control systems (ICS).
The hackers behind Snake use an exposed RDP instance with weak passwords to access and infect an ICS environment. Once the program is within the system, Snake encrypts data via a mix of symmetric and asymmetric cryptography.
Snake does not attack the operating system files or programs. Infected computers still boot up, but Snake prevents access to target data.
23. WastedLocker
WastedLocker started to hit businesses in May 2020. Notorious for high ransom demands, hackers behind WasteLocker ask for millions of dollars per victim.
WasteLocker is an example of targeted ransomware. Every attack has a custom plan to breach a specific company. Ransom messages always refer to the victim by name, and all encrypted files have the .garminwasted extension.
WasteLocker encrypts data with a combination of AES and RSA algorithms. What sets this ransomware apart is that a single public RSA key encrypts files. Most other programs generate a unique public RSA key for each infection.
Keeping your data safe 24/7 and eliminating the risk of data loss is much easier with the right provider. Learn more about our Ransomware Protection Solutions.
Ransomware is a Question of When, Not If
Companies must not ignore the danger of ransomware. The ever-growing number of attacks guarantees most businesses will face this threat at some point. Use our guide for preventing ransomware to ensure your business’ safety. Make sure not to miss our article How to Use Immutable Backups to Fight Ransomware.