Social engineering has become a malicious tool for hackers to conduct cyber attacks.
Virus protection or your firewall won’t help if you are duped into clicking a malicious link thinking it came from a colleague or social media acquaintance.
Here’s what you need to understand to stay safe and protect your data.
What is Social Engineering?
By definition, social engineering is an attack vector used to gain access to gain access to networks, systems, or physical locations, or for financial gain by using human psychology, rather than using technical hacking methods. It relies on social interaction to manipulate people into circumventing security best practices and protocols.
Social engineering is the new preferred tactic among the hacker community. It is easier to exploit users’ flaws than to discover a vulnerability in networks or systems.
Understanding different types of social engineering attacks is an essential aspect of protection.
TYPES OF SOCIAL ENGINEERING THREATS
Phishing
Phishing is one of the most common types of social engineering.
When a website, article, or online community is presented to a targeted individual as authentic and secure but instead uses a URL that is not official it is called phishing. Hackers and thieves alike utilize phishing attacks to gain false hope and trust from potential victims to receive sensitive information such as usernames, email addresses, and passwords that are linked to social media accounts and bank login websites. Phishing involves the participation of users for the theft of information and data to be completed.
Phishing is most common among users who are not well-versed in browsing the internet or those who are new to using social media and online resources to search for information, content, and media. Many phishing attacks target individuals who are elderly or those who do not work in the tech industry to obtain sensitive information without the risk of being caught.
Preventing phishing starts by ensuring each URL you visit is official and authentic. Phishing attacks often target social media platforms, banking websites, and online service sites to gather crucial information from users who fall for the faked URL.
Phishing attempts increased by 30 million from 2017 to 2018, according to Kaspersky Lab.

Baiting
Baiting is used in both the digital and physical world.
Baiting consists of leaving devices in public areas that are packed with malware, spyware, or other damaging software which is then used to steal and collect the information of users who are tempted to see the contents of the device.
Most commonly, flash USB drives are left in areas such as bathrooms, libraries, subway stations, or even on airplanes in hopes to attract the curiosity of individuals.
Once the user plugs the device into their computer, malware is downloaded onto the hard drive.
Keyloggers and malicious software then send data directly to the hacker, allowing them access to websites and accounts.
Digital baiting is also found in advertisements that showcase enticing deals or free items, only to lead users to websites that immediately trigger a download of malware and spyware software.
In some cases, malware and spyware programs are disguised as traditional software or software updates.
When browsing for software, it is imperative to verify the authenticity of the URL and the provider.
Spear Phishing
Spear phishing is designed to personally attack an individual or organization to appear more authentic and legitimate.
Spear phishing attacks often utilize a user’s personal information or details about an individual to gain the trust and curiosity of the user before stealing information, installing malware, or delivering a keylogger to the individual’s hard drive. Hackers who use spear-phishing tactics are well-versed in scraping data of users from social media sites, official blogs, and even email newsletters or previous online leaks and security breaches.
When a user is presented with a spear phishing attack, they are likely to feel that the attack is a genuine attempt to share information, content, or free products due to the overwhelming personal details provided.
Spear phishing is becoming more popular than traditional phishing attacks as users become aware of checking URLs and verifying the websites they shop and browse on whenever they are online. With a spear phishing attack, it becomes increasingly difficult to determine whether or not the URL or information is malicious, even for those who are seasoned internet users.
Tailgating
Tailgating is a social engineering threat that is purely physical and involves real-world interaction to work. When a hacker is interested in obtaining the information of a specific individual or organization, they may follow them to local cafes or locations where free Wi-Fi is available. Hacking into a public Wi-Fi hotspot provides thieves with the ability to learn more about individuals using the connection while obtaining sensitive and personal data.
Other forms of tailgating may include asking an individual to utilize their access pass while entering a building or going to work in their office by lying about forgetting their pass to quickly steal information. Tailgating is often used by hackers who have a vested interest in an individual or organization believed to have wealth or unsecured banking accounts that are easy to hack and steal from once access is provided.
Tailgating is one of the most personal forms of social engineering and also one of the most threatening in the real world.
Remaining vigilant and secure when accessing Wi-Fi hotspots or internet anywhere outside of the home is essential to prevent the risk of exposing personal information and data that belongs to you. It is also necessary to maintain an encrypted and protected internet connection to keep potential hackers from obtaining access to your data.
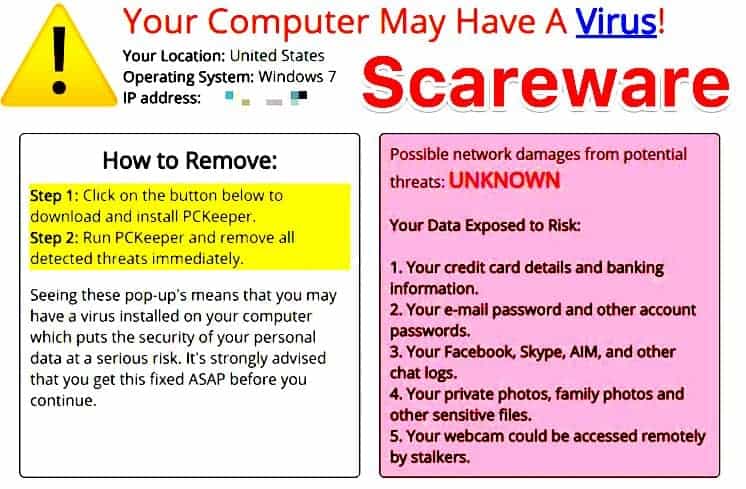
Scareware
Scareware is extremely successful in obtaining user information and financial details.
Often presented as popups or programs while prompting users with warnings or threats to receive information such as names, credit card details, and even social security numbers.
An individual is likely to be threatened with contact from the FBI or other areas of the government, prompting quick responses to avoid further action. When users are unfamiliar with this tactic, they are much more likely to fall for a scareware attack.
Scareware does not always include personal or direct threats. Scareware is also commonplace when browsing on unofficial websites or sites that provide free content or programs that are otherwise not free.
In many cases, scareware is used to prompt individuals to download malicious software due to a threat of spyware or malware already infecting the user’s hard drive.
Once the individual downloads the solution presented by the scareware campaign, their computer is compromised and hackers then gain direct access to personal information or the entire hard drive itself.
Pretexting
Pretexting scams are used to collect personal information from individuals by impersonating police, government officials, bank account managers, or even co-workers.
Hackers use pretexting to target unsuspecting individuals who are likely to feel threatened or fearful of retribution if they do not share the requested information. Pretexting is done over the phone, via email, or in some cases, even with the use of social media messenger applications.
Perpetrators who use pretexting often inform individuals that they are in need of highly sensitive information to complete a task or to prevent the individual from legal trouble.
When an individual feels threatened, vulnerable, or scared, they are much more likely to reveal bank account numbers, routing numbers, social security numbers, and other sensitive data.
Quid Pro Quo
Quid pro quo involves hackers requesting information from unsuspecting individuals with the promise of offering something in return.
Individuals presented with a quid pro quo attack are likely to receive offers of compensation, free vacations, or gifts such as new products that are most relevant to the individual’s lifestyle.
Quid pro quo attacks occur over the phone, while using social media, or even through traditional email newsletters that have been hacked, compromised, or impersonated. Users are presented with the promise of money, free travel, or gifts in exchange for login information, credential verification, or other sensitive details such as social security numbers and bank account and routing numbers.
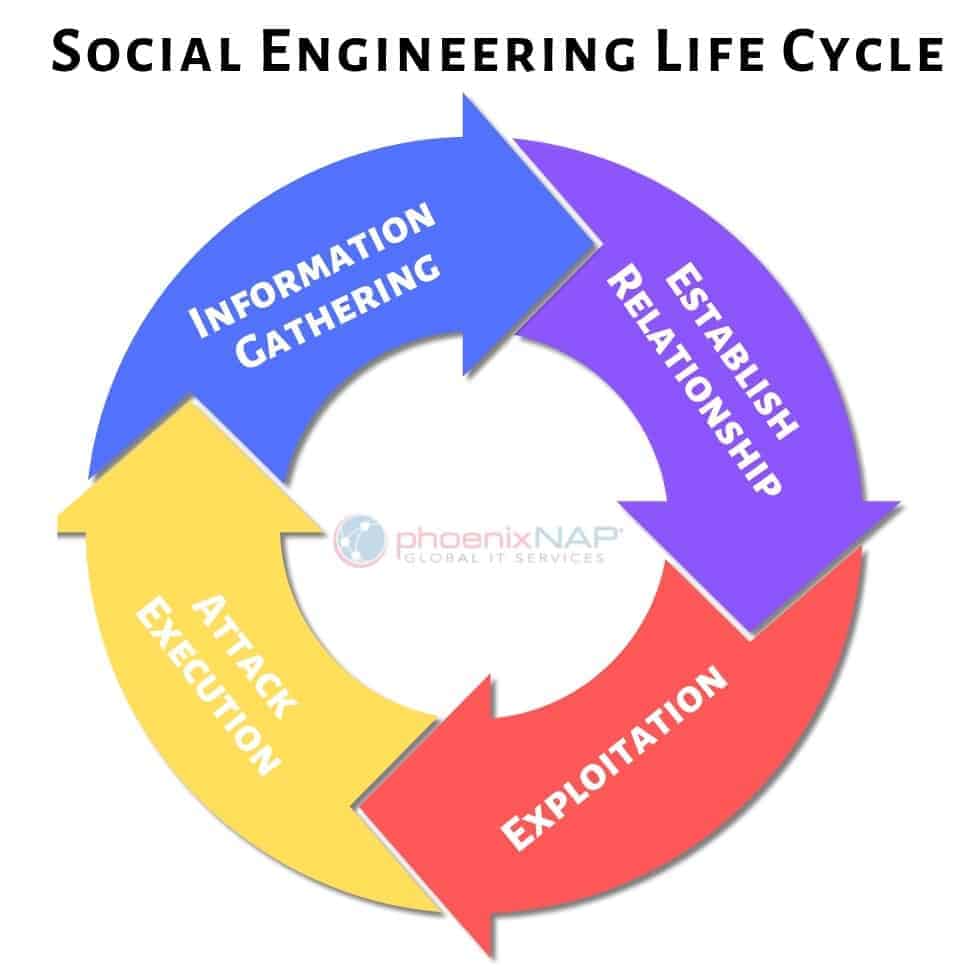
3 Phases of Social Engineering
Research Phase
The first phase of any social engineering attack is research. During this phase, attackers search for information about you. The easiest route to find potential information is through a web or social media search. Social media security best practices are key as people often post personal information that attackers can use against them.
If the target is a business, attackers may be able to collect information about employees or security rules that may aid future attacks. Managers and other high-value targets are at a higher risk because attackers are more likely to do more research for these targets.
Skilled social engineers often research what companies you might work with. They can then use this information to better pretend to be a technician or consultant with the company to gain access to sensitive areas. Through this pretext, they may trick targets into revealing sensitive or secure data.
Contact Phase
After the research phase has finished, attackers will move on to the contact phase. During this phase, attackers will use researched information to look for other weaknesses and gain the target’s trust. This often includes pretending to be someone the target trusts. Once the victim trusts the attackers, the attackers can then leverage this for more information or access.
For example, attackers might use social media to find which employees of a company have left for vacation. They might then contact the company pretending to be a vacationing employee who forgot to give them important information before leaving. Knowing that one employee was out of the office, another person at the company might try to help them by sending attackers the desired information.
Attack Phase
The attack phase builds on the previous two phases. In most cases, this means that attackers have the necessary information and access to you or your company’s systems.
Basic attacks will use this access to steal information from a system, but some hackers go further. Advanced attacks will use this access to aid them in future attacks. They might then leave a backdoor into the system, or copy your credentials.
Understand Social Engineering Threats
Social engineering is not new. However, it is becoming the go-to attack vector of hackers.
With a clear understanding of the definition of social engineering, take control of your online activity while remaining protected.