Cybersecurity has become a top concern as more companies store data and provide services online. This increased digital presence makes them vulnerable to cyber-attacks, which can lead to devastating financial losses and reputational damage.
This article outlines essential cybersecurity best practices every business should implement. By following these strategies, you can build a strong defense against cyber threats, safeguard your valuable data and systems, and protect your business's future.

The Importance of Proper Cybersecurity Measures
The importance of cybersecurity cannot be overstated in an age where data breaches, phishing attacks, and malware incidents are becoming more frequent and sophisticated. To highlight this issue, here are some headline statistics from recent years:
- More than 60% of enterprise data is now stored in the cloud, reflecting a shift in how companies operate and manage their information. This transition to cloud storage has expanded the attack surface for potential cyber threats, making cloud security a top priority for organizations.
- A staggering 72% of businesses worldwide reported being affected by ransomware attacks in 2023, marking a significant increase compared to previous years and the highest figure on record. This trend highlights the growing threat of ransomware to businesses of all sizes, with the healthcare sector disproportionally targeted.
- Data breaches are becoming more expensive, with the global average cost of a data breach reaching a record $4.45 million in 2023.
- Sixty-two percent of organizations believe their cybersecurity teams are understaffed, underscoring the growing gap between the number of professionals needed to defend against cyber threats and the available skilled workforce.
- Seventy percent of cybersecurity professionals claim the cybersecurity skills shortage has impacted their organization.

Cybersecurity Best Practices
These best practices address various aspects, from technical solutions to policy and training – all vital for protecting your business from increasingly sophisticated threats.
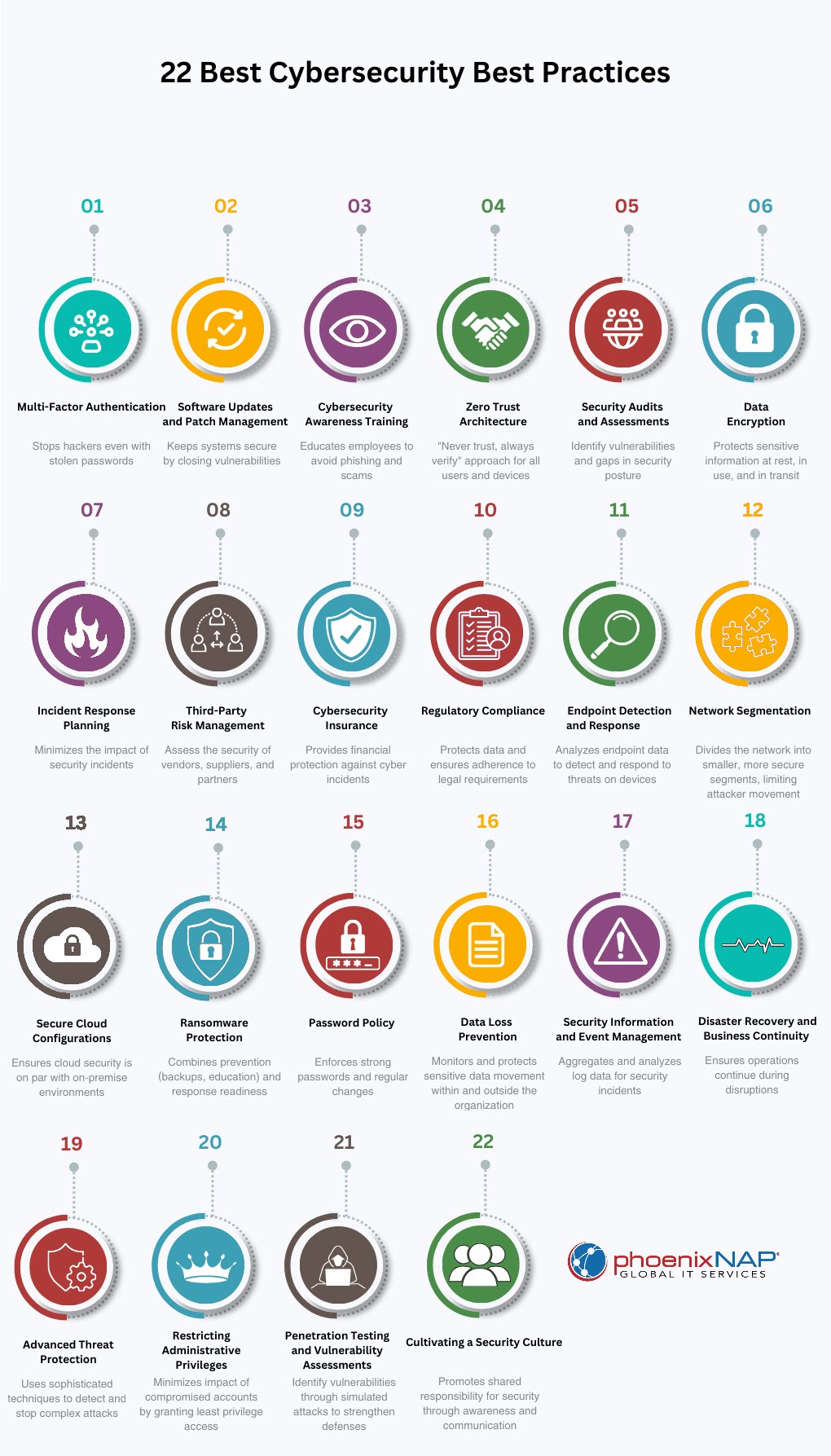
1. Multi-Factor Authentication
Multi-factor authentication (MFA) is a critical element of enhanced access security. It goes beyond single-factor password-based methods, which hackers can breach through phishing, social engineering, or brute force attacks. MFA requires users to provide two or more verification factors to gain access, significantly reducing the risk of unauthorized access due to compromised credentials.
A recent statistic published by Microsoft suggests that MFA can block over 99.9% of account compromise attacks.
2. Software Updates and Patch Management
Regular software updates and patch management are essential for maintaining the integrity and security of systems. By keeping software up-to-date, organizations can close known vulnerabilities that attackers exploit.
An effective patch management strategy prioritizes patches based on the severity of vulnerabilities and the system's criticality.
3. Cybersecurity Awareness Training
Security awareness training tackles the human element in cybersecurity, often considered the weakest link. According to IBM data, over 90% of cyber-attacks exploit human error.
Tailored training for different user groups and regular refresher sessions are crucial for reducing the risk of employees falling victim to phishing scams, social engineering, or unintentionally compromising security. Additionally, incorporating practical exercises like phishing simulations helps employees recognize and respond effectively to real-world threats.
4. Zero Trust Architecture
Zero trust architecture upgrades network security by adopting a principle of "never trust, always verify" for all devices and users, regardless of location. This approach relies on three key pillars:
- Rigorous identity verification.
- Network segmentation to restrict lateral movement.
- Least privilege access control, minimizing user exposure to sensitive areas.
Gartner predicts that by 2023, over 60% of enterprises will adopt a zero-trust security model.
5. Security Audits and Assessments
Regular security audits and assessments are essential to identify vulnerabilities and gaps in an organization's security posture. These evaluations should employ both automated scanning and manual review for comprehensive analysis.
Security audits often reference established frameworks and standards like SOC 2 to ensure thorough coverage of potential issues, such as misconfigurations, unnecessary services, and weak policies exploitable by attackers.
6. Data Encryption
Encryption is the foundational element of a data protection strategy, protecting the confidentiality and integrity of sensitive information, even during unauthorized access.
Organizations should encrypt data at rest, in use, and in transit using robust encryption standards and secure key management practices. Furthermore, it is critical to address the entire lifecycle of encrypted data, including secure deletion procedures.
7. Incident Response Planning
An incident response plan equips organizations to effectively manage and minimize the impact of security incidents. It establishes the cyber incident response team (CIRT) and their responsibilities, creates communication protocols, and details containment, eradication, and recovery procedures.
Regular testing and updates through simulations ensure the plan's effectiveness.
8. Third-Party Risk Management
Third-party risk management is crucial, as 59% of data breaches involve third parties. Extending security beyond the organization's direct control involves assessing the security posture of vendors, suppliers, and partners to ensure alignment with the organization's security standards.
By 2025, 60% of organizations are expected to prioritize minimizing cybersecurity risks when choosing partnerships.
9. Cybersecurity Insurance
Cybersecurity insurance provides a financial cushion against the rising costs of cyber incidents. As the frequency and sophistication of these threats increase, cyber insurance enables organizations to recover from financial losses. However, it's essential to carefully review policies to ensure they align with your organization's specific risks.
The global cybersecurity insurance market is expected to reach $22.1 billion by 2025.
10. Regulatory Compliance
Compliance with regulations and industry standards is a legal mandate and a pathway to robust security. Stay informed of relevant regulations like GDPR, HIPAA, and PCI-DSS and implement controls and policies to achieve compliance.
Regular audits identify and address any gaps and ensure consistent adherence.
11. Endpoint Detection and Response
Endpoint Detection and Response (EDR) solutions offer continuous monitoring and analysis of endpoint data to detect threats and safeguard endpoint security. These advanced platforms identify malicious activities and indicators of compromise (IOCs) that may evade traditional security measures.
By isolating compromised devices and facilitating swift incident response, EDR solutions help organizations prevent the spread of malware and minimize the impact of many types of cyber-attacks.
12. Network Segmentation
Network segmentation divides the network into smaller, more manageable segments, each with its own set of access controls. This strategy limits an attacker's ability to move laterally within the network and access sensitive areas.
Effective segmentation is based on a thorough understanding of data flows and the principle of least privilege, ensuring users and devices can only access the network resources necessary for their roles.
13. Secure Cloud Configurations
Securing cloud configurations is essential for leveraging the dynamic and scalable nature of cloud computing while maintaining security controls comparable to on-premise environments. Organizations must adopt a comprehensive cloud security strategy that includes identity and access management (IAM), encryption, and secure configuration of cloud resources.
Continuous monitoring for misconfigurations and unauthorized changes ensures that the environment remains secure.
14. Ransomware Protection Strategies
A robust anti-ransomware strategy requires both prevention and response readiness. Preventive measures, like a backup strategy, advanced threat detection, and user education, significantly reduce the risk of attacks.
However, being prepared to respond through an incident response plan designed explicitly for ransomware and the ability to restore systems from backups swiftly is critical to minimize downtime and data loss.
15. Password Policy Enforcement
Strong password policies safeguard access to systems and data, as 44% of individuals admit to reusing passwords across personal and business-related accounts. Therefore, enforcing complex passwords, mandating regular password changes, and utilizing password managers are foundational to maintaining password security.
Training users on the importance of strong passwords and the risk of reuse further reinforces these technical controls.
Check out phoenixNAP's free password generator to generate a secure, random password.
16. Data Loss Prevention
Data Loss Prevention tools monitor and protect the movement of sensitive data within and outside the organization. These solutions help prevent the unauthorized transfer and sharing of sensitive information, helping organizations comply with regulations and protect intellectual property.
Tailoring DLP policies to the organization's data classification framework guarantees appropriate protection for private information.
17. Security Information and Event Management
Security Information and Event Management (SIEM) systems aggregate and analyze log data across the organization to detect, alert, and respond to security incidents. By correlating events from various sources, SIEM can identify anomalous behavior and potential security incidents that single systems might not detect.
This centralized view is critical for timely incident response and effective security monitoring.
18. Disaster Recovery and Business Continuity Planning
Disaster recovery and business continuity planning is vital to an organization's ability to remain operational during major cyber incidents or disasters. Identifying critical systems, data, and processes and establishing plans for recovery and continuity are key to building resilience.
Regular testing and updates ensure these plans remain effective as the organization and its technology evolve.
19. Advanced Threat Protection
Advanced Threat Protection (ATP) systems employ sophisticated techniques to detect and thwart attacks that elude traditional security measures. Leveraging machine learning, behavioral analysis, and threat intelligence, ATP can identify and neutralize intricate threats such as zero-day exploits and advanced persistent threats (APTs).
Integrating ATP with other security systems strengthens the organization's security posture by creating a layered defense.
20. Restricting Administrative Privileges
Restricting administrative privileges based on the principle of least privilege reduces the potential impact of a compromise. Regular audits of user roles and permissions and the implementation of role-based access control (RBAC) ensure users have only the necessary access to perform their duties. This restriction minimizes the risk of accidental or malicious changes to critical systems and data.
21. Penetration Testing and Vulnerability Assessments
Penetration testing and vulnerability assessments offer insights into an organization's security posture by simulating real-world attacks. Conducted by skilled security professionals, these tests evaluate the effectiveness of security controls and identify vulnerabilities that could be exploited.
The findings guide the prioritization of remediation efforts, strengthening the organization's defenses against potential attackers.
22. Cultivating a Security Culture
While technical solutions are vital, building a security culture is equally important. This culture inspires employees to actively protect sensitive information and encourages shared responsibility for security across the entire organization.
Effective communication is key to this approach. Regularly communicating clear and concise security policies, highlighting the importance of good security practices, and acknowledging successes significantly enhances employee awareness and engagement. Additionally, analyzing security incidents constructively, learning from mistakes, and implementing improvements demonstrates the organization's commitment to continuous learning and adaptation.
Concerned about cloud security? Consider phoenixNAP’s Data Security Cloud, a secure infrastructure platform built in collaboration with Intel and VMware. It provides multi-layered data protection through a secure hardware foundation, strict virtualization and segmentation controls, threat intelligence, and advanced physical security.
Focus on your business, not security breaches. Choose Data Security Cloud!
Maintaining Cybersecurity
Cybersecurity is not a one-time fix. The digital environment is constantly evolving, with new vulnerabilities emerging every day.
Organizations must consistently implement cybersecurity best practices and stay informed about emerging threats to stay protected.



