Agile software development and DevOps Security go hand in hand.
Agile development focuses on changing how software developers and ops engineers think. A DevOps approach focuses on the underlying organizational structure, culture, and practice of software development.
In the past, the two functions were separate. Developers wrote the code. Ops implemented and managed it.
However, a developer’s complex code was sometimes clumsy to implement, causing pushback from operations. DevOps addresses the tension and, in some cases, downright hostility between the two functions.
What is DevOps Security?
Combining the words “development” and “operations,” DevOps security breaks down the barriers between software development and IT operations.
Instead of developers coding, then throwing it over the wall to operations, DevOps puts the teams together. Driven by (CI/CD) continuous integration DevOps practices and a continuous deployment philosophy, faster, agile release cycles replace big releases.
This work environment keeps software developers and IT operations in constant communication and tightens collaboration. The combined teams launch software and infrastructure with fewer errors that cause outages, release rollbacks, and operational disruptions. DevOps is a two-pronged approach that addresses cultural change while transforming technology and tools.
Businesses that adopt this approach gain the following benefits:
Consistency
Standardizing infrastructure provisioning and the software release process enforces consistency across the entire DevOps environment.
Provisioning
Code new instances in a few keystrokes using automation tools and runbooks that turn manual processes into pre-packaged, automatic actions.
Speed and Agility
Increase agility, quality, and reliability of new software launches and feature releases.
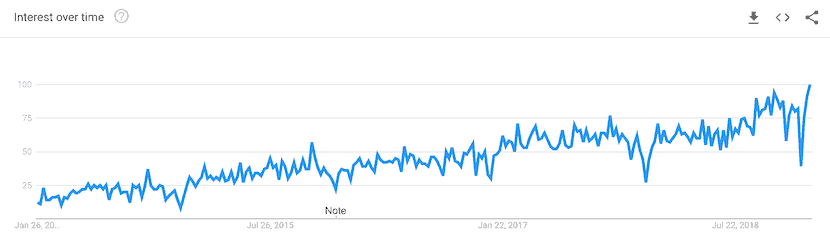
Google Trends reflecting increased interest in DevOps.
DevOps Security Challenges
Though DevOps solves many challenges in the software development process, it also introduces new challenges. Less than 46% of IT security professionals are skipping DevOps security in planning and design. These environments end up with a reactive, uncoordinated approach to incident management and mitigation. Often, the lack of coordination isn’t evident until an incident occurs, and systems are breached or attacked.
Aside from just a blip in operations, security breaches can reap long-term havoc. Take the case of the 2017 Uber breach. The root cause was a careless developer who published credentials to GitHub. An all too common error when quickly compiling code to keep up with agile development cycles.
Hackers quickly pounced, attacking Uber in a breach that impacted over 50 million customers and nearly 600,000 drivers. Uber paid off the hackers to keep quiet. However, the data breach was eventually discovered and led to a public relations nightmare.
A secure DevOps environment runs on different tools, processes, and policies to facilitate rapid and secure releases. In the case of Uber, a final security scan to ensure no credentials are left embedded in the code. These pieces come together to provide bulletproof security throughout the application development, release, and management phases.
Organizational Opposition
In the desire to move quickly, security is often seen as just one more thing to slow down the release process. As a result, developers start to resent the time needed pre-release to do security checks, which creates vulnerabilities.
Security Vulnerabilities in the Cloud
Firewalls can’t completely protect you in the cloud. Securing in the cloud revolves more around RBAC and access management. Many of the processes and tools used in securing DevOps rely on cloud-based resources.
Legacy Infrastructure
In that same SANS study referenced above, over 90% reported that they were still supporting legacy resources. That leaves most organizations running hybrid environments using cloud-based elements with traditional, legacy infrastructure. The performance and security requirements of legacy resources create complications when folded into DevOps environments.
Recruiting
As a new discipline, finding experienced DevSecOps engineers is not only difficult, but also pricey. The average salary for DevSecOps engineers is $131,000. The effort to get existing staff up to speed and production-ready potentially impacts attention to critical daily operations.

What Does DevSecOps Stand For?
DevSecOps is a philosophy that brings security into the software development process as a shared responsibility.
The fundamental principle is that everyone involved is accounting for security. It also integrates automated security tasks within DevOps (a type of agile relationship between development and IT operations) processes.
The “Sec” in DevSecOps is security. In the past, application security wasn’t a primary concern for developers. Many companies treated security as an afterthought. Sometimes that meant taking on security features at the end of development. Sometimes, it wasn’t considered unless there was a breach.
Before the rise of cybercrime, there weren’t many financial reasons for security. It didn’t add value—or at least it didn’t seem to. Customers were left to look out for themselves. Security companies jumped in to write antivirus programs and firewalls, but this didn’t solve security for individual products or applications.
Data breaches became more frequent, and penalties grew more severe. Customers got frustrated, and companies started seeing higher costs associated with low security. With securing in development, the DevSecOps model creates shared responsibility between Development, Security, and Operations.
How Can You Utilize DevSecOps?
DevSecOps works by protecting against the new type of risks that CI/CD introduces within a DevOps testing framework.
Extensive security checks once saved for the end of the development cycle, become integrated while the code is being built. DevSecOps covers code analysis, post-deployment monitoring, automated security controls, and other security checks. By remaining engaged throughout the process, bugs and other potential issues are uncovered and mitigated before launching.
The result is a more cohesive experience in the development process and a better end-user experience. The improved delivery chain gives users updated features faster, more secure software, and allows users to focus on their jobs instead of lagging technology.
Automated controls and reporting tools help to maintain security, compliance, and privacy to meet stringent compliance and legal regulations. Many of these functions can be automated for reporting and audit purposes. This can often be the tipping point for stakeholders concerned about the risk involved in fast-moving DevOps environments.
DevSecOps best practices include:
- Leaning in over always saying “No”
- Data and security science vs. fear, uncertainty, and doubt
- Open contribution and collaboration over security-only requirements
- Consumable security services with APIs over mandated security controls
- Business-driven security scores over “rubber stamp” security
- ‘Red and Blue Team exploit testing over scans and theoretical vulnerabilities
- 24×7 proactive monitoring versus overreacting after an incident
- Shared threat intelligence over keeping information to silos
- Compliance operations over clipboards and checklists
DevSecOps vs DevOps
DevOps methodology evolved from two industry practices, Lean and Agile.
In the early days of software, engineers wrote most applications. Business leaders set the specifications, and the software engineers would build applications to match. Users, support staff, and security had very little input during development. This led to apps that had lots of features but were harder to learn. It also created long development times and significant waste.
To trim the efficiency of software developers, businesses applied the Lean model. Lean manufacturing sought to reduce waste. By keeping only the parts that add value, companies could make software development more efficient. The Lean model also makes people more critical in the process. The goal with Lean was to get better software by improving the development process.
Lean grew another development philosophy, called Agile. Agile is a set of guidelines created by software engineers but aimed at business leaders. It focuses on communication, working together, and rapid change. These features helped software companies respond more quickly to the market by shortening development cycles. It also helped companies respond better to customer feedback.
The Lean and Agile models helped businesses break out of the old, clunky development model.
To improve software development, a model was needed that focused just on software development. That’s when DevOps was created. “Dev” refers to development, meaning anyone involved in writing software. “Ops” means anyone who operates the software, from users to support agents.
In DevOps, both teams are involved in writing software.
With operations involved, developers don’t need to wait on publication or testing to get feedback. Operations are included and help developers adjust to make better software.
With these two development teams working together, apps can be better, intuitive, and easy to use. It also shortens the development cycle, putting review alongside development. Overall, this process leads to continuous delivery of new software features and updates.
Why The Change In Software Development Model?
Traditionally, a company implemented security after the software was created. It can be an easier way to include security but often works like a retrofit job. When the developers are finished, security reviews the software, and any changes are just tacked on.
Another security model is to compare finished software to an existing security policy. Any areas where the software doesn’t pass policy are kicked back to the developers.
Both of these methods are widely used, and often necessary. Some platforms are used for decades and need to be adjusted as technology moves forward. Usually, the market changes and software has to keep up. Or, an older feature like a database holds critical information, but it may not work with newer servers. Due to the high cost of rebuilding the database, some companies pile on updates and security features. This creates a compromise between cost and security.
A policy of patching at the end of development has its problems. One issue is that it tends to put the focus on reacting to incidents, instead of preventing them. One example of this is modern operating systems. The developer of an operating system publishes regular updates. These updates fix security flaws that are found during testing. This is an important process! However, hackers closely watch that list of updates. Then, they write viruses and scripts that exploit those very weaknesses. And it works, because many companies have a lag between when the patch is released and when it’s installed. Some companies are even stuck using older, unsupported operating systems. With no patches available, a company is stuck with either expensive upgrades or possible security breaches.
With security testing being so complicated, some organizations see it as an obstacle.
The original DevOps model promoted speed and flexibility. Sometimes application security vulnerability is just put on the back burner, or even ignored entirely in the name of speed. This can help companies get an edge in a competitive market. However, with recent, massive data breaches, the “patch later” plan can be a costly gamble.
Advantages of Developing with DevOps Security
DevSecOps promotes a culture of security.
This is useful when developing an application because built-in security features are more effective and more accessible to enhance. The culture of security can also seep into the rest of the business. Operation teams may see the value in security measures, and avoid bypassing them to simplify their work. Developers have a clear view of the finished package they can build to. Security teams become partners and collaborators, instead of reviewers and critics.
One of the critical values of integrating collaboration with a security team is mindfulness. Security practitioners on the development team help everyone to be more aware of security.
That translates into developers making better choices while planning and writing software. It also means operations teams are more likely to promote secure practices and procedures.
Another feature of implementing security into DevOps is that its part of the natural structure. DevOps brings operations into software development. It’s a natural extension to bring Security in. With this in mind, operators are more likely to find ways to misuse apps and fix them, rather than let them slide. They may suggest effectively, but less intrusive, threat protection features.
Implementation earlier in development helps to make security an integral part of the process. That might look like simple, secure authentication. It could also mean less retrofit security. In creating a coherent approach, everything works seamlessly together. Presenting a unified front acts as a strong deterrent against cyber attacks.
Automation of security best practices can be done using scripts or automated testing tools. Use automatic monitoring scans that only read the code that’s been changed. Consider doing regular security audits.
Automated security testing reduces the time spent reviewing an application and overall costs.

How To Implement Best Practices of DevSecOps
Shifting to a DevSecOps model isn’t just a change in technology. It helps to think of it more as a change in philosophy. Adopting integrates security into the fabric of applications and business processes.
One way to implement DevSecOps is to bring security professionals in alongside developer teams and operations teams. Have security teams conduct testing in development, just as they would run tests on IT infrastructure. The details might vary, but the overall process should resemble standard security services.
There are a few more target areas to focus on:
- Use a change management service. These platforms track projects, privileged users, and changes to the code. This helps bring continuous delivery and integration of code changes to everyone involved.
- Analyze code in smaller units. It is easier to scan, and any changes can be corrected more quickly.
- Maintain proper operations and security procedures. If an audit is done regularly (as it should be), your teams are more likely to pass. This also helps promote a culture of good security practices, which in turn lowers overall risk.
- Compare new features and updates against evolving threats. Cyber attacks are becoming more complex. It’s critical always to be aware, and take measures to secure your environment against them.
- When apps are in production, keep evaluating them. Look for new vulnerabilities and fix them. Evaluate and improve how quickly they can be fixed.
- Cross-train developer and operation teams in security, and vice-versa.
If you’re familiar with, implementing security shouldn’t be too challenging.
Consider it as a way of building function, ease-of-use, and security at the same time. DevSecOps training creates coherent software that’s secure and intuitive.
Meeting The Challenges of DevSecOps
There’s often a clash of culture between security and DevOps teams. The disconnect results from developers using agile development methodologies while security teams are holding on to older waterfall methodologies. As developers push to move faster, they often see the advanced security processes as a hindrance.
To keep up with development, DevSecOps integrates automated security controls. Baked into the CI/CD cycle, they require minimum human intervention – and little risk of error. In a DevSecOps survey, 40% reported performing automated security checks throughout the entire software development cycle as opposed to just pre-launch.
Intelligent Automation
Tools like Checkmarx, Splunk, Contrast Security, Sonatype, and Metasploit automate security analysis and testing throughout the software development process.
An embedded static application security testing (SAST) tool scans applications for security issues once a day. To scan an application in real-time, opt for dynamic application security testing (DAST) to find vulnerabilities as they occur.
Open Source Safety
Open source code helps developers quickly implement features, but it also introduces security risks. Recent research shows that 96% of all applications contain open source components. Unfortunately, only 27% of respondents have a plan for identifying and mitigating flaws in open source software.
DevOps tools like OWASP Dependency-Track and GitHub automate the process of checking for flawed open source elements.
Mind Your Alerts
Though these automated tools can shoot out alerts on thousands of different parameters, don’t overwhelm your team. If developers get slowed down with too many alerts, you run the risk of them going around or ignoring warnings.
Start with a few alerts to get them used to it and only apply real-time alerts for critical errors. Set static alerts for a broader set of factors. Balance the need to know with the capacity to respond.
Threat Modeling
Categorizing potential threats, determining the possible outcome, and creating a proactive mitigation strategy results in a solid threat model. By preparing for possible scenarios, you can implement the right tools and processes to reduce the impact of an incident.
To automate the process of threat modeling, use tools like OWASP Threat Dragon and Microsoft Threat Modelling Tool.
Paced Security Transformation
No matter how anxious an organization is to start using secure DevSecOps, remember to focus on small goals. Many DevSecOps security projects fail because the goals exceed capabilities, resources, or talent.
It Is Time To Shift to a DevSecOps Mindset
DevSecOps demands a change in the organizational mindset.
For security teams, it’s a commitment to not being the “no” and to find more ways to say “yes.” This means finding more agile ways to secure assets leveraging automation and machine learning.
For an organization, it means embracing a security-first mindset that incorporates security into the full development lifecycle. This means not sacrificing necessary security measures in the pursuit of CI/CD speed.
If you would like to learn more about practices that automate crucial security tasks and ensure close collaboration between security and operations teams, we suggest you check out our article on what is SecOps.