Software applications are the backbone of many industries. They power many businesses and essential services. A security lapse or failure in such an application can result in financial loss, as well as a tarnished reputation. In some extreme cases, it can even result in loss of life.
What Is DevSecOps?
DevSecOps is the method that integrates security practices within the DevOps process. It creates and promotes a collaborative relationship between security teams and release engineers based on a ‘Security as Code’ philosophy. DevSecOps has gained popularity and importance, given the ever-increasing security risks to software applications.
DevSecOps integrates security within your product pipeline in an iterative process. It thoroughly incorporates security with the rest of the DevOps approach.
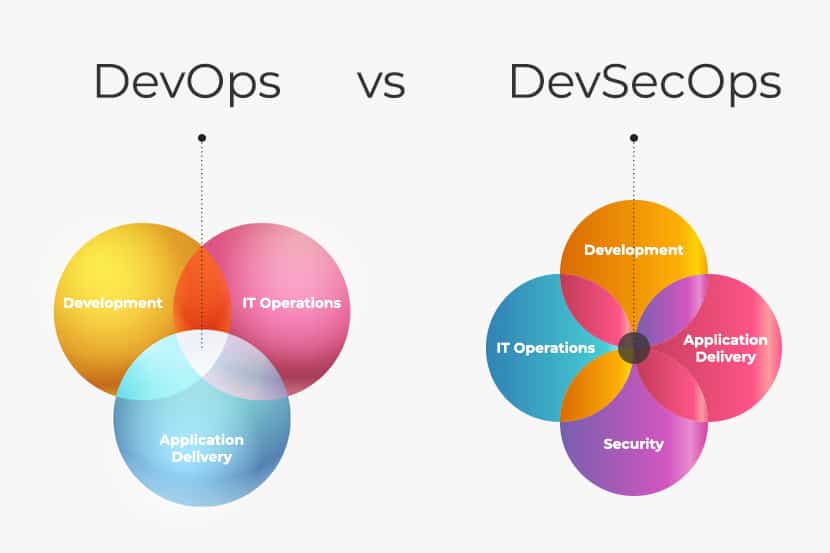
As teams develop software, testing for potential security risks and flaws is critical. Security teams must address issues before the solution can move ahead. This iterative process will ensure that vulnerabilities do not go unaddressed.
As DevSecOps is still a new and emerging discipline, it may require some time to gain mainstream acceptance and integration. A significant amount of security tests take place late in the production cycle. This delay can cause major issues for companies and their products. As security is usually is one of the last features considered in the development process. If you keep security at the end of the development pipeline, when security issues come up near launch, then you will find yourself back at the start of long development cycles.
When security concerns are raised late in the production cycle, teams will have to make significant changes to the solution before rolling it out. An interruption in production will ultimately lead to a delay in deliverables. Thus, ignoring security issues can lead to security debt later in the lifecycle of the product. This is an outdated security practice and can undo the best DevOps initiatives. So the DevSecOps goal is to begin the security team’s involvement as early as possible in the development lifecycle.
How Does DevSecOps Work?
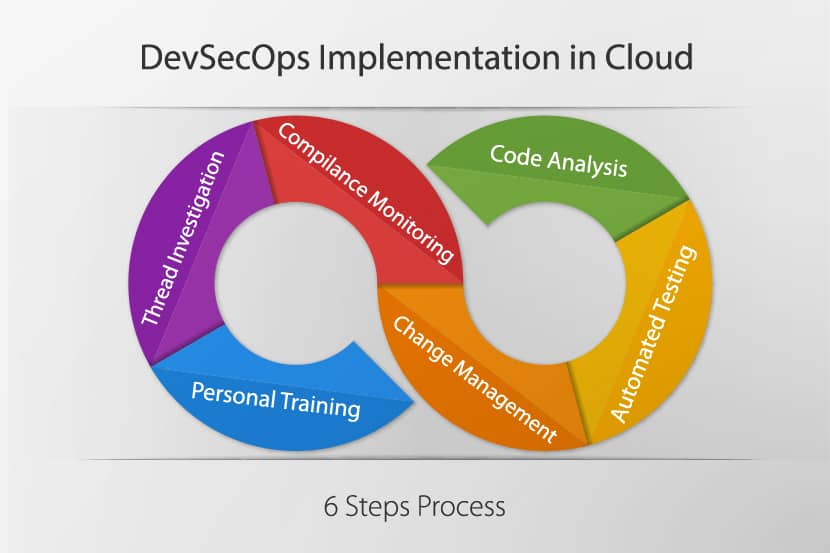
The DevSecOps method needs development and operations teams to do more than just collaborate. Security teams also need to join in at an early stage of the iteration to ensure overall software security, from start to end. You need to think about infrastructure and application security from the start.
Not only does consistent testing lead to secure code, but it also avoids last-minute delays by spreading the work predictably and consistently throughout the project. Through this process, organizations can better achieve their deadlines and ensure that their customers and end-users are satisfied.
IT security needs to play an integrated role in your applications’ full life cycle. You can take advantage of the responsiveness and agility of a DevOps approach by the incorporation of security into your processes.
The primary areas of software security testing are being adopted:
Application Security Testing
As software applications are run, solutions can scan the application to ensure that malicious actions are not being taken. Scanners such as Burb Intruder and OWASP Zap automation will test and examine applications, to ensure that they aren’t taking steps that could be perceived as malicious by end-users.
Scanning for the Appropriate Configurations
Software tools can be designed to ensure that the application is configured correctly and secured for use in specific environments, such as the Microsoft Azure Advisor tool for cloud-based infrastructure. Many automated testing tools are designed to operate in a particular environment, such as a mobile environment or web-based environment. During the development of software, it can be ensured that the software is being built to these appropriate standards.
Code Analysis Tools
Code analysis tools can strengthen DevOps security efforts by automatically scanning the code and identifying potential and known vulnerabilities within the code itself. This can be invaluable information as the software teams work, as they will be able to identify problems before they are caught in quality assurance. This can also help them in developing better coding habits.
DevSecOps Best Practices
DevSecOps integrates security into the development lifecycle, but it is not possible to do so hastily and without planning. Include it in the design and development stages. Companies can work to change their workflows by following some of the best practices of the industry.
Get Your Teams on Board
It may seem trivial, but getting all the required teams working together can make a huge difference in your DevSecOps initiative. Development teams are familiar with the typical process of handing off newly released iterations to Quality Assurance teams. This isolated behavior is the norm in companies that have each team in a silo.
Companies should eliminate silos and bring development, operations, and security teams together. Unity across teams will enable the experts in these groups to work together from the beginning of the development process and foresee any challenges.
Threat modeling is one way to plan for and identify possible security threats to your assets. You examine the types and sensitivities of your assets and analyze existing controls in place to protect those assets. By identifying the gaps you can address them before they become an active problem.
These types assessments can help identify flaws in the architecture and design of your applications that other security approaches might have missed.
The first step in implementing a DevSecOps culture is to educate your teams that security is a shared responsibility of teams from all three disciplines. Once development and operations teams take on the shared responsibility of securing code and infrastructure, DevSecOps becomes a natural part of the development cycle.

Many DevOps teams still have the misconception that security assessment causes delays in software development and that there should be a trade-off between security and speed. DevSecOps events and training are excellent opportunities to rid teams of these misconceptions. Real-life examples and case studies can help to get buy-in from teams and management alike.
Educate Your Developers
Developers are almost single-handedly responsible for the quality of the code they develop. Coding errors are the cause of many security vulnerabilities and issues. But companies pay little attention to their developers’ training and skill enhancement when it comes to producing secure code.
Educating them in the best practices of coding can directly contribute to improved code quality. Better code quality leaves less room for security vulnerabilities. Security teams will also find it easier to assess and remedy any vulnerabilities in high-quality code.
‘Common software weaknesses’ is another area in which most developers are unfamiliar. Teams can use online tools like the Common Weakness Enumeration list as a reference. Listings are useful to developers who are not that familiar with security practices.
Security teams, as part of their commitment to DevSecOps, must undertake to train development and operations teams regarding security practices. Such training will enable developers to integrate security controls into the code.
Compliance (HIPAA, GDPR, PCI) is vital for applications in industries such as finance and medicine. Development teams must be familiar with these standards and keep in mind the requirements to ensure compliance.
Verify Code Dependencies
Very few organizations today develop their code all in-house. It is more likely that each application will be built on a large amount of third-party, open-source code.
Despite the risk, many companies use third-party software components and open-source software in applications instead of developing from scratch. Yet they lack the automatic identification and remediation tracking for bugs and flaws that may exist in open-source software. Due to the pressure of meeting customer demands developers rarely have the opportunity to review code or documentation.
This is where automated testing plays a significant role in regularly test open-source and third-party components. It’s a main requirement in the DevSecOps methodology. It’s critical to find out if open-source usage is causing any weaknesses or vulnerabilities in your code. You need to find out how it impacts dependent code. It will help you identify issues that help reduce the meantime to resolution.
Third-party code can represent some significant vulnerabilities. Organizations will need to identify their code dependencies and automate the process of ensuring that their third-party code has no known vulnerabilities and is being updated as it should be throughout the process of creation.
There are utilities available that can continuously check a database of known vulnerabilities to quickly identify any issues with existing code dependencies. This software can be used to swiftly mitigate third-party threats before they are incorporated into the application.
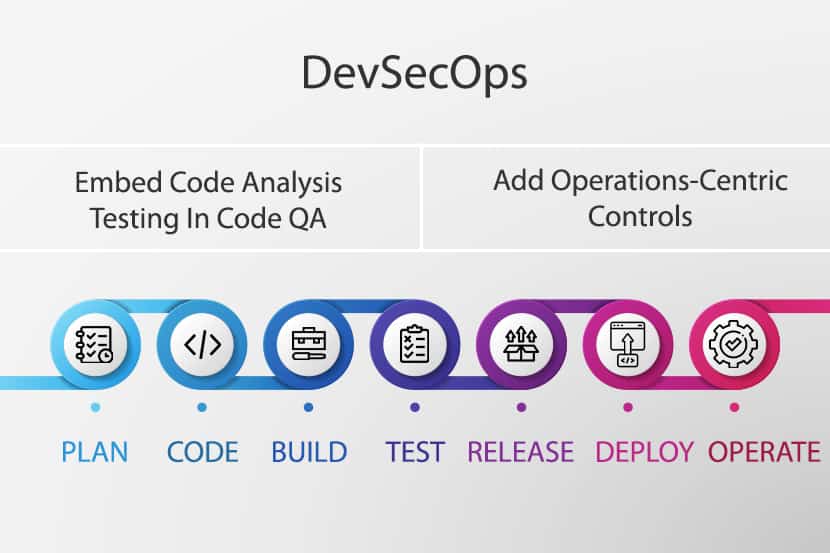
Enhance Continuous Integration with DevOps Security
DevOps teams typically use Continuous Integration (CI) tools to automate parts of the software development cycle, such as testing and building. These are routine tasks that teams need to repeat with each release.
Enhancing Continuous Integration processes and tools with security controls ensures that security practitioners identify issues before validating builds for Continuous Delivery (CD). CI also reduces the time spent on each iteration.
For example, using (SAST) static application security testing on daily builds will help you ensure that you’re only scanning for instances or items of interest in the changes to your code that were committed that day.
DevSecOps teams need to use vulnerability assessment scanning tools to ensure that they identify security issues early in the development cycle. They can use pre-production systems for this type of testing.
Simplify Your Code
Simpler code is easier to analyze and fix. Developers will find debugging their code much easier when it is simple and easier to read. Simple and clean code will also lead to reduced security issues. Developers will be able to quickly review and work on each other’s code if it is simple.
More significantly, security teams will be able to analyze simple code more efficiently. So releasing code in smaller chunks will allow security teams to identify issues sooner and with less effort. By choosing one section to analyze and prove it works, before moving on to the next bit will streamline the process. It will reduce the probability of security vulnerabilities and leads to robust applications.
Security as Code
‘Security as Code’ is the concept of including security best practices into the existing DevOps pipeline. One of the most critical processes that this concept entails is the static analysis of code. Security practitioners can focus testing on code that has changed, in contrast to analyzing the entire code base.
Implementing a good change management process will allow members of all teams to submit changes and improvements. This type of process will enable security teams to remedy security issues directly without disrupting the development cycle.
Automation is another essential aspect of ‘security as code.’ Teams can automate security tasks to ensure that they conventionally verify all iterations. This uniformity will help to reduce or eliminate the presence of known security issues. Automation can significantly reduce the time spent on troubleshooting and fixing security issues later in the development cycle.
Put Your Application Through Security Checks
Your application should be subject to regular testing. It should also undergo more rigorous testing such as preventing denial of service attacks.
There may be vulnerabilities in a solution that are only evident when that solution is broken. These are still genuine problems that the product owner may face.
Organizations are seeing an increasing number of malicious attacks. These attacks may focus on any aspect of a client’s organization that is accessible from outside of the network.
By testing your application under particularly strenuous circumstances, you can secure it through various scenarios.
How to Implement DevSecOps?
Each of the teams involved in DevSecOps needs to contribute towards its success.
Development
Developers perform an essential role in the DevSecOps process. Developers must be open to the involvement of operations and security teams. The participation of these teams from an early stage of the design and development process will facilitate a secure DevOps transformation and make applications overall more secure.
Training developers in security best practices is essential to success. Companies can supplement this training with hiring developers who have experience in DevSecOps so that they can guide the rest of the team.
Companies must build a culture where developers are aware that developing security is a shared responsibility between them and security teams. Security practitioners can only recommend security practices. It is the responsibility of developers to implement them.
Operations
The contribution of the operations team is similar to that of the development team. Operations teams must collaborate with security practitioners. They are responsible for subjecting infrastructure and network configurations to security tests.
Security teams will also need to train operations teams regarding security practices to make DevSecOps successful. Operations and security teams, in collaboration, will then set up both manual and automated security tests to ensure compliance with network configurations.
Security
DevSecOps is as much of an adjustment for security teams as it is for development and operations teams. Security teams have to gradually increase their involvement while cooperating with development and operations teams.
Security practitioners should start with the concept of ‘shifting left.’ That is, collaborating with development and operations teams to move security reviews and automated tests towards the beginning of the software development lifecycle. This process of shifting left is essential to reduce the chances of unforeseen security issues popping up later.
Development and operations teams usually see security tests as a tedious and complicated task. So the duty of security teams does not stop at developing security tests but extends to involving and training the other teams.
DevSecOps is the Future
DevSecOps methodology has gained momentum due to the high cost of correction of security issues and security debt. As Agile teams release applications more frequently, security testing becomes more crucial. We hope some of the best practices mentioned in this article will help your company to transition from DevOps to a DevSecOps approach.