An SQL injection (SQLi) is among the most predictable, easy-to-defend-against types of cyberattack. Unfortunately, SQL injections are also among the most effective cybercrime tactics, primarily because they are easy to pull off, and many businesses fail to implement the necessary countermeasures.
An SQLi also has devastating consequences (data breaches, intruders gaining root access, account misuse, etc.), which is why preventing injections must be at the top of your cybersecurity to-do list.
This article will take you through everything a security team must know about SQL injections. We will explain what SQL injection is, show the different tactics hackers use to exploit SQL-related flaws, and present the most effective ways to protect a database from SQLi attempts.
SQL injections are a major threat to databases, but not the only one. Learn what else you must account for in our guide to database security.
What Is SQL Injection?
An SQL injection (SQLi) is a cyberattack in which someone injects malicious SQL statements into an application to compromise files within the associated database. Criminals use SQLi to target apps and websites that rely on an SQL database (i.e., MySQL, Oracle, PostgreSQL, Microsoft SQL Server, etc.).
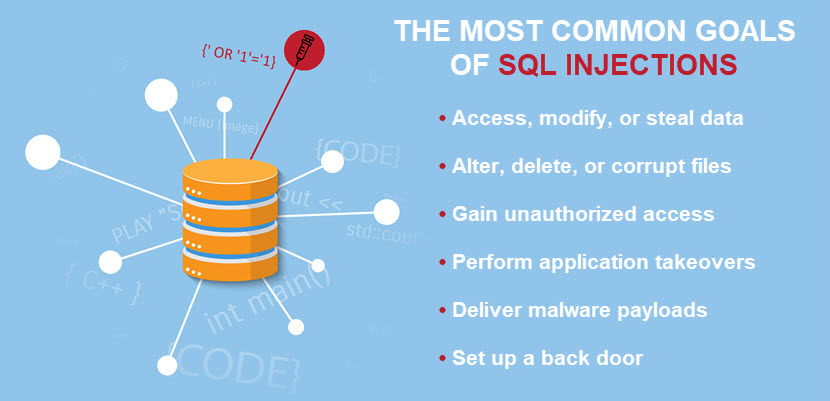
SQL injections typically occur due to poor input validation and a lack of proper parameterization in SQL-based apps. Attackers exploit these flaws to trick the app into executing unintended commands on the database server, enabling hackers to:
- Access data.
- Extract files.
- Delete or modify data.
Most SQLi vulnerabilities arise within the WHERE clause of a SELECT query. However, a flaw can occur at any location within the query. Other common locations where SQLi flaws arise are:
INSERTstatements (within inserted values).SELECTstatements (within table/column names or theORDER BYclause).UPDATEstatements (within updated values or theWHEREclause).
If there's an exploitable flaw in the database, an SQL injection is simple to pull off even by a novice hacker. Attackers typically find vulnerable targets using advanced Google searches (so-called Google Dorking) and then feed found URLs to an automated bot that carries out injections.
Despite this simplicity, some of the world's biggest brands have fallen victim to SQL injections in the past few years (LinkedIn, Target, Yahoo, Equifax, 7-Eleven, Epic Games, Zappos, TalkTalk, Sony Pictures, etc.).
Our MySQL commands cheat sheet offers an overview of the most important commands you need to master this RDBMS.
SQL Injection Statistics
Here are a few recent must-know statistics concerning SQL injections:
- In 2022, 1162 new SQLi vulnerabilities were added to the CVE (Common Vulnerabilities and Exposures), the database of publicly disclosed info on security issues.
- SQL databases were the main source of web app vulnerabilities in 2022, accounting for around 33% of all flaws.
- Two out of three web attacks include an attempt to inject a malicious SQL command.
- Security experts suspect that 21% of organizations currently have an exploitable SQL-related vulnerability.
- In 2022, around 42% of all hacking attempts on public-facing systems were SQL injections. The threat extends to internal systems but to a lesser degree (approx. 12%).
- Research suggests a record-high 35% of educational institutions have an exploitable SQLi vulnerability.
Interested in more cybersecurity-related statistics? Check out the following articles:
Potential SQL Injection Consequences
SQL injections often have severe and far-reaching consequences for organizations that fall victim to these attacks. Here's what malicious actors can accomplish with an SQL injection:
- Analyze the database and learn about its version and structure, info that becomes valuable in future attacks (e.g., a ransomware payload intended to encrypt specific files in a database).
- Retrieve sensitive data from the database (e.g., usernames, passwords, email addresses, credit card details, etc.).
- Modify, insert, or delete files within the database, causing corruption and a loss of data integrity.
- Obstruct an app's logic.
- Exploit server resources and cause performance degradation or crashes.
- Bypass the authentication mechanism and gain access to an account without knowing the credentials.
- Escalate privileges and gain access to the underlying server.
- Disrupt normal business operations and cause downtime, loss of revenue, and customer dissatisfaction.
- Use the underlying server to launch a DDoS attack.
- Deploy malware or set up resources for more advanced breaches (e.g., an APT attack).
Depending on the nature of breached data and applicable laws, an SQL injection can also lead to legal actions and regulatory penalties.
How Does SQL Injection Work?
An SQL injection occurs when a hacker sends malicious SQL queries (requests to perform some action on an app database) to a website or web-based service through a form or search box. An attacker submits specially crafted input that includes SQL code alongside legitimate data. That way, a hacker tricks the app into executing unintended SQL commands.
For example, a web-based app has a login form with two fields, one for usernames and the other for passwords. The app constructs the following SQL query to check the validity of credentials when someone submits an input:
SELECT * FROM users WHERE username = 'input_username' AND password = 'input_password';
So, when a legitimate user types in "admin1" as a username and "SuSIOP8f&)@^Sx2" as a password, the following SQL statement executes against the database server:
SELECT * FROM users WHERE username = 'admin1' AND password = 'SuSIOP8f&)@^Sx2';
This query then authenticates the user who provided valid credentials. However, an attacker might input the following in the username field:
' OR '1'='1
Once the app submits this request, the query becomes:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'input_password';
Since '1'='1' is always true, the query effectively becomes:
SELECT * FROM users WHERE username = '' OR true AND password = 'input_password';
This manipulated query allows an attacker to bypass the password check and gain unauthorized access. The query returns all rows where the username is empty or true.
In most cases, there are no indications that someone is performing SQL injections on a database. The only sign of an attack is an excessive number of requests within a short time frame, a red flag that often goes unnoticed by the security team.
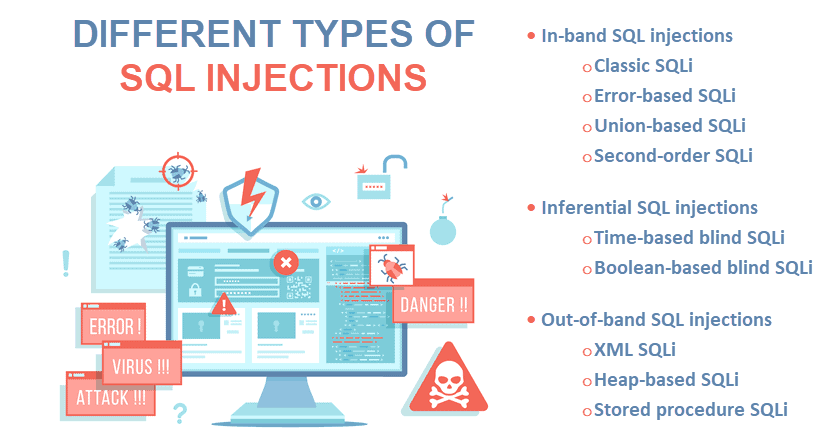
SQL Injection Types
There are three main types of SQL injections based on how an attacker interacts with the target app and its database: in-band, inferential, and out-of-band SQL injections. Let's take a closer look at each category.
In-Band SQL Injections
In-band SQL injections occur when an attacker uses the same communication channel (i.e., band) to launch the attack and gather results. The malicious actor sends manipulated SQL code, and the app's response provides direct feedback about the attack's success.
Here are the different in-band SQL injection techniques:
- Classic SQL injections: An attacker injects malicious SQL code into an input field to manipulate the database query. Classic injections are the go-to option to bypass authentication or retrieve files from the database.
- Error-based SQL injections: A hacker intentionally triggers SQL error messages to collect info about the database schema or content.
- Union-based SQL injections: An attacker uses the
UNIONSQL operator to combine the results of the original query with results from another query. That way, an attacker retrieves data from other tables in the database. - Second-order SQL injections: A malicious actor does not execute the input but stores it in a database. The stored input activates in a new SQL query when a user accesses some specific functionality of the app.
In-band tactics are the most common type of SQL injection. These attacks are also easier to pull off than other inferential or out-of-band SQLi.
Inferential SQL Injections (Blind SQLi)
Inferential SQL injections happen when an attacker sends malicious SQL code but does not receive direct feedback from the target app. Instead, the attacker infers info from the server's behavior (hence the term "blind SQLi").
There are two distinct types of inferential SQL injections:
- Time-based blind SQL injections: A hacker uses delays in SQL queries to gauge the app's responses and infer info about the database. For example, a hacker could use an SQL query to command a three-second delay if the first letter of the first database's name is A. If the response takes three seconds, the attacker knows the query is valid.
- Boolean-based blind SQL injections: An attacker sends a series of boolean-based you-or-no questions to the web app's database. The hacker observes the app's behavior and gradually gathers info about the database structure and content.
An inferential SQL injection is a common choice for someone trying to map the database structure.
Out-of-Band SQL Injections
Out-of-band SQL injections occur when someone sends malicious SQL code to the target app and tricks it into sending data to a remote endpoint controlled by the attacker. Here are the most common out-of-band SQL injections techniques:
- XML SQL injections: If an app uses XML queries to interact with a database, a malicious actor can manipulate input data to inject malicious XML code and alter the query's behavior.
- Heap-based SQL injections: This type of SQL injection targets the app's memory allocation mechanism. An attacker injects malicious input to disrupt or corrupt the app's memory, causing crashes or gaining unauthorized access.
- Stored procedure injections: This technique targets apps that use stored procedures to interact with the database. An attacker injects malicious input into the procedure's parameters to gain access to or manipulate data.
Out-of-band techniques are the least common and most complex type of SQL injection. Hackers turn to these methods if the target server is too slow or unstable for inferential or in-band SQL injections (or in specific cases when an app blocks or sanitizes certain types of responses).
How to Prevent SQL Injection?
Below are some of the most effective ways to ensure your database never falls victim to an SQL injection.
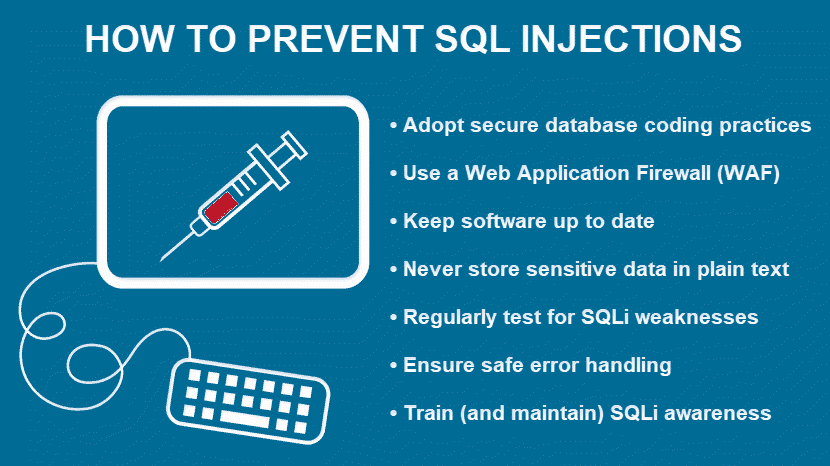
Adopt Secure Database Coding Practices
Adopt secure database coding practices and principles to ensure developers write code resistant to common SQL-related exploits.
Here are a few practices that are highly effective at preventing SQL injections:
- Validate and sanitize all user inputs.
- Allow only expected input formats and characters in your forms.
- Use parameterized queries and prepared statements when interacting with databases.
- If parameterized queries or prepared statements are not an option, escape user input before including it in a query to convert potentially dangerous characters into safe equivalents.
- Store sensitive data (passwords, API keys, tokens, etc.) in secure configuration files or environment variables instead of hard-coding data into the codebase.
- Avoid constructing queries dynamically using string concatenation.
- Use output encoding to ensure data displays as content and not executable code.
- Conduct regular peer code reviews to identify and fix potential vulnerabilities.
Additionally, ensure developers only use well-established security libraries and frameworks that went through thorough reviews.
Use a Web Application Firewall (WAF)
A Web Application Firewall (WAF) filters all traffic between the web app and your database. WAFs analyze incoming traffic and inspect data for:
- Known attack patterns.
- Anomalies.
- Suspicious behavior.
A WAF relies on various techniques to identify and block malicious requests (e.g., signature-based detection, behavioral analysis, machine learning, etc.). These firewalls block SQL injection attempts in real time before they reach your database code.
Read about the different types of firewalls and see whether some might be worth adding to your IT defenses.
Keep Software Up to Date
Organizations must keep software up to date with the latest security patches. Ensure the following elements have the latest updates:
- Operating systems.
- Web servers.
- Database management systems (MySQL, PostgreSQL, Microsoft SQL Server, etc.).
- Content management systems (WordPress, Joomla, Drupal, etc.).
- App frameworks (Django, Ruby on Rails, Laravel, etc.).
- Firewalls.
- Web browsers.
- Third-party libraries, frameworks, plugins, and extensions.
- Authentication and authorization libraries.
- Server software (e.g., SSH, FTP, remote management tools, etc.).
Additionally, if your web-facing apps integrate with third-party APIs or services, ensure they're using the latest versions of their software.
Never Store Sensitive Data in Plain Text
Encrypting valuable data ensures that even if an attacker manages to extract files with an SQL injection, the stolen data remains unreadable without the decryption keys.
Implement encryption both for data at rest (stored in the database) and in transit (transferred between the app and the database). Remember that your encryption strategy is only as good as your key management practices, so ensure your team knows how to keep cryptographic keys safe.
Regularly Test for SQLi Weaknesses
Testing for SQL injection vulnerabilities is a critical part of preventing attacks. Here are a few worthwhile practices:
- Regularly review your source code to identify potential SQL injection vulnerabilities. Pay special mind to areas where queries directly use web-based user inputs.
- Experiment with known SQL injection payloads to check your app's resistance to standard attack techniques.
- Manipulate inputs to trigger database errors and analyze whether messages reveal anything of value.
- Use automated vulnerability scanning tools to identify common flaws quickly.
- Perform both white-box (with knowledge of the app's internal workings) and black-box tests (without internal knowledge).
- Always test inputs with special characters, SQL keywords, and payloads to ensure proper sanitation.
- Test how your app and database handle parameterized queries and prepared statements.
- Inject queries that cause server delays and observe the differences in how long the app takes to respond.
- Test for boolean-based injections with queries that rely on true/false conditions (e.g., OR 1=1 and OR 1=2).
- Check how your app responds to different
UNIONqueries. - Submit the single quote character in your input field and look for errors or other anomalies.
- Submit an
OASTpayload designed to trigger an out-of-band network interaction when executed within an SQL query. Then, check for any resulting interactions.
Remember to perform SQL injection testing regularly. It's an excellent idea to do a few checkups whenever the team makes significant code changes, updates, or feature additions.
You also have the option to organize penetration tests, either on an in-house level or by outsourcing ethical hackers. These realistic attack simulations identify more complex vulnerabilities that traditional tests often miss.
Ensure Safe Error Handling
Never display detailed error messages on the client web browser. Instead, provide generic error messages or user-friendly pop-ups that do not share insights into your app's inner workings.
Error-based SQL injections are a popular tactic for system reconnaissance, so ensure a malicious actor cannot learn anything useful by intentionally causing errors.
Train SQLi Awareness
Educate your team about the risks, techniques, and best practices related to SQL injections to improve your security posture. Organize regular cybersecurity training sessions for all technical staff (software developers, QA, SysAdmins, DevOps teams, etc.).
High awareness of SQLi threats reduces the overall attack surface for injections. Knowledgeable developers are also more likely to write secure code and identify flaws in the early stages of development.
Despite being relatively easy to prevent, SQL injections proved to be among the most common cyberattacks in 2023. Learn what other cybersecurity trends are currently on the rise and see whether your security strategies require some updating.
A Well-Prepared Company Should Never Fall Victim to SQLi
SQL injections are a common hacking technique with often severe consequences. Therefore, it's vital to protect your business from this threat. Luckily, following best practices and periodically testing for flaws is enough to counter the risk of SQLi. Set up the precautions discussed in this article and ensure your databases are not vulnerable to SQL injections.



