Introduction
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are often mentioned when talking about the Internet and Website security. To make matters even more confusing for the laymen, these terms are often used interchangeably.
But how do TLS and SSL actually work, and are there any differences you should be aware of?
In this tutorial, we will explain the TLS and SSL security protocols, the differences between them, and which one you should use.
TLS vs SSL
Both TLS and SSL work as cryptographic protocols that are used to encrypt data between a web server and users.
The original version of SSL was developed by Netscape in 1994 but was never officially released due to easily exploitable security flaws. An upgraded version 2.0 was released in February 1995, but it had serious flaws of its own, which would be patched by SSL 3.0 only a year later.
TLS was conceived by Consensus Development as an upgrade of SSL 3.0. It was released in 1999 and would be replaced in 2006 by TLS 1.1, which added protection against CBC (Cipher Block Chaining). In 2008, TLS 1.2 added a further set of upgrades, with the latest version being TLS 1.3, released in 2018.
While TLS and SSL are fundamentally similar, considering that TLS 1.0 was based on SSL 3.0, there are still differences in the way they work:
| SSL | TLS | |
|---|---|---|
| Cipher Suites | Offers support for Fortezza cipher suite. | Offers support for RC4, Triple DES, AES, IDEA. |
| Alert Messages | “No certificate” alert message. | Different alert messages depending on the situation. |
| Record Protocol | Uses MAC (Message Authentication Code). | Uses HMAC (Hash-Based Message Authentication Code). |
| Handshake Process | Hash calculation includes the master secret and pad. | Hashes are calculated over the handshake message. |
| Message Authentication | Ad-hoc method of adjoining key details and application data. | Adjoining key details and application data through HMAC. |
A Matter of Handshakes
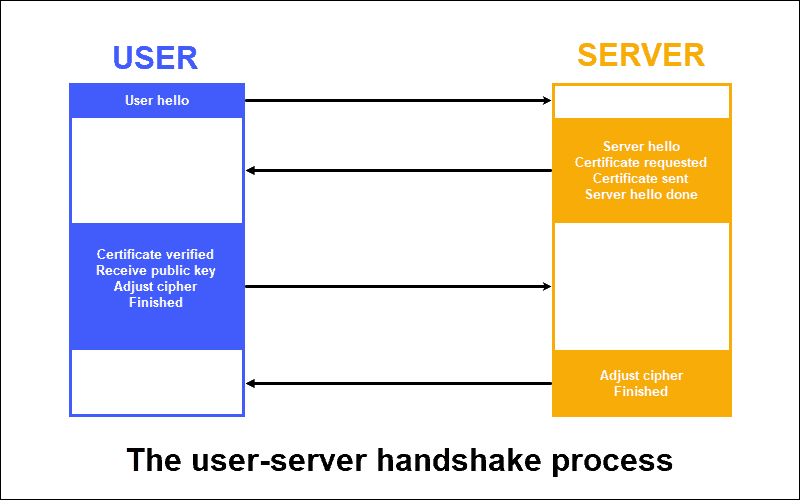
A “handshake” refers to the part of the communication process between a web server and a user that establishes a secure connection and determines which type of encryption is used.
In general terms, both the SSL and TLS handshake process follows these steps:
1. The end-user’s system requests a secure connection and receives a list of cipher suits, algorithmic toolkits used to encrypt data, from the server. The system compares this with its own list of cipher suits and selects one that both it and the server can use.
2. The sever provides a digital certificate as proof of identity. The user’s machine receives the certificate and confirms its authenticity.
3. Using the server’s public key, the end-user’s system and the server agree on a session key they use to encrypt data.
Note: As the name implies, a session key is only used for a single communication session. If the connection between the user and server in interrupted for any reason, a new session key is created once the communication is restored.
When performing a handshake, SSL uses a port to establish connection (by default, this is port 443). TLS, on the other hand, begins the first step of the handshake (requesting a secure connection) via an unsecured channel, and switches to port 443 once the handshake begins.
How Do TLS and SSL Work to Secure Data?
As we discussed above, the handshake process involves the server sending a digital certificate and public key to the end-user’s system to establish a secure connection. Installing an SSL certificate/TLS certificate authenticates the web server and provides public and private keys that are used during the handshake.
Without a certificate, a user attempting to access the web server receives a “your connection is not private” error message. This signals to the user that their data may be exposed and is likely to cause them to leave your website.
Should You Use TLS or SSL?
These days, both SSL and earlier versions of TLS are considered obsolete. SSL 2.0 and 3.0 were deprecated by IETF in 2015, while TLS 1.0 and 1.1 were deprecated in early 2020 and are currently being removed from new versions of browsers.
When choosing between the two, TLS is the obvious choice. It does not only serve as an upgrade to SSL, but also performs much better.
Note: Newer versions of web browsers have stopped supporting SSL and are encouraging website owners to move to TLS. For instance, Google Chrome started displaying the ERR_SSL_OBSOLETE_VERSION warning on websites that still use SSL.
How to Check Which TLS/SSL Protocol is Enabled?
If you are not sure whether a web server is using an obsolete TLS/SSL version, you can quickly check by using a web browser.
In Google Chrome and Microsoft Edge, right-click on a blank area of a webpage and click Inspect. In the Inspect window, under the Security tab, find an overview of the website’s digital certificate.
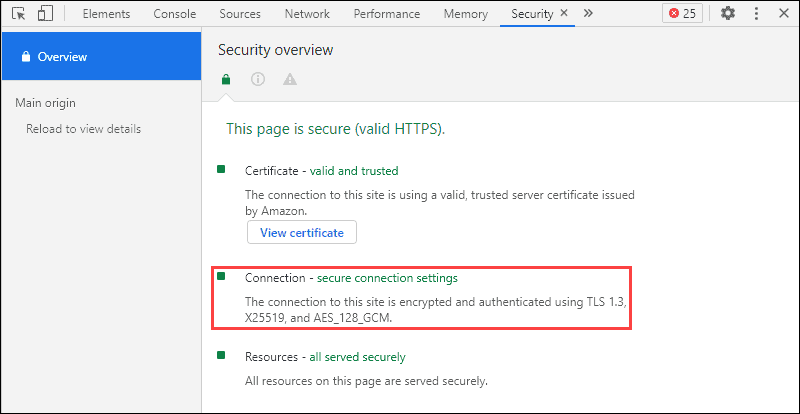
Using Firefox, right-click the page and click View Page Info. You will find the details of the digital certificate under the Security tab.
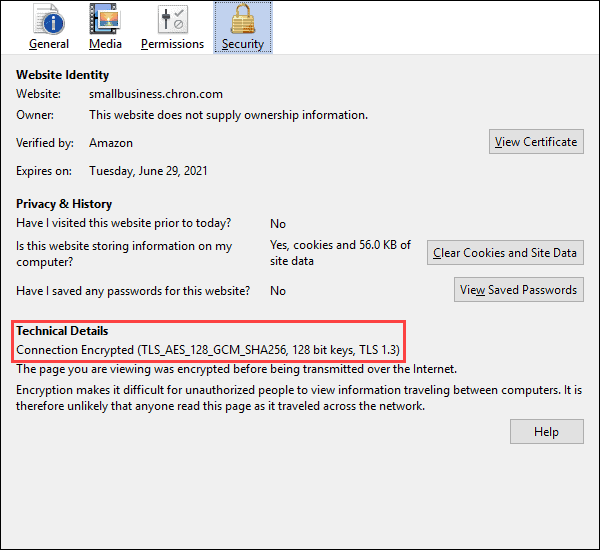
Alternatively, use an online TLS/SSL checker tool.
How to Disable Older Versions of TLS and SSL?
TLS 1.3 is the latest and safest cryptographic protocol used to establish safe communication between a user’s system and a web server. Deprecated versions of TLS and SSL pose a security risk due to security vulnerabilities. For security reasons, disable SSL versions 2 and 3, and TLS versions 1.0 and 1.1 on live servers.
The only permitted protocols on a web server should be TLS 1.2 and TLS 1.3.
The steps to disable SSL 2.0 or 3.0, or TLS 1.0 depend on whether the server is using Apache, NGINX, or Tomcat.
Apache
To disable SSL 2 and 3, and TLS 1.0 and 1.1 on an Apache server, follow the steps below.
1. Locate the Apache configuration file. The default file location depends on your system:
- On Debian/Ubuntu based systems, the default file location is
/etc/apache2/apache2.conf - On Debian/Ubuntu based systems configured in a virtual host, the default file location is
/etc/apache2/sites-enabled/ - On Red Hat/CentOS based systems, the default file location is
/etc/httpd/conf/httpd.conf - On Red Hat/CentOS based systems configured in a virtual host, the default file location is
/etc/httpd/sites-enabled/
2. Open the configuration file and find the SSLProtocol entry.
3. Edit the entry to disable SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.14. Restart the Apache service for the changes to take effect:
service apache2 restartor
service httpd restartNote: Depending on your server configuration, you may need to make these changes in multiple places, not just in the default configuration file.
NGINX
To disable SSL 2 and 3, and TLS 1.0 and 1.1 on an NGINX server, follow the steps below.
1. Find the NGINX configuration file. The default location of the global configuration file is /etc/nginx/nginx.conf, but there may be individual server block configurations in /etc/nginx/sites-enabled/.
2. Edit the configuration file to enable TLS 1.2:
ssl_protocols TLSv1.2;3. Restart the NGINX service:
service nginx restartNote: Learn how to install an SSL certificate on NGINX.
Tomcat
To disable SSL 2 and 3, and TLS 1.0 and 1.1 on a Tomcat server, follow the steps below.
1. Find the Tomcat configuration file. The default location is TOMCAT_HOME/conf/server.xml.
2. Edit the configuration file to enable TLS 1.2.
- For Tomcat 5 and 6 (prior to 6.0.38):
sslProtocols = "TLSv1.2"- For Tomcat 6 and 7 (6.0.38 or newer), edit the following line:
sslEnabledProtocols = "TLSv1.2"3. Restart the Tomcat service for the changes to take effect.
Conclusion
While there are still many websites using SSL, if you want to follow the most up-to-date security recommendations, you should switch your website to TLS 1.2 or 1.3.
Not only do TLS 1.2 and 1.3 make a website more secure, with the addition of HTTP/2, they also increase speed and performance.
Next, read our guide on SSL certificate types to ensure you pick the right one for your website or web app.