Introduction
Data transmission between devices on a network needs to be regulated for devices to communicate properly. The transmission is carried out with a set of rules known as a network protocol.
Early network protocols like Telnet and rsh did not provide enough protection against malicious cyber attacks. The need for a more secure network communication method inspired the creation of the SSH protocol.
In this tutorial, we will talk about what SSH is, why it is used, and how it works.
Note: The tutorial will talk about SSH2, the current version of the protocol. The original SSH is now considered outdated and less secure.
What is SSH?
SSH (short for Secure Shell) is a network protocol that provides a secure way for two computers to connect remotely. SSH employs encryption to ensure that hackers cannot interpret the traffic between two connected devices.
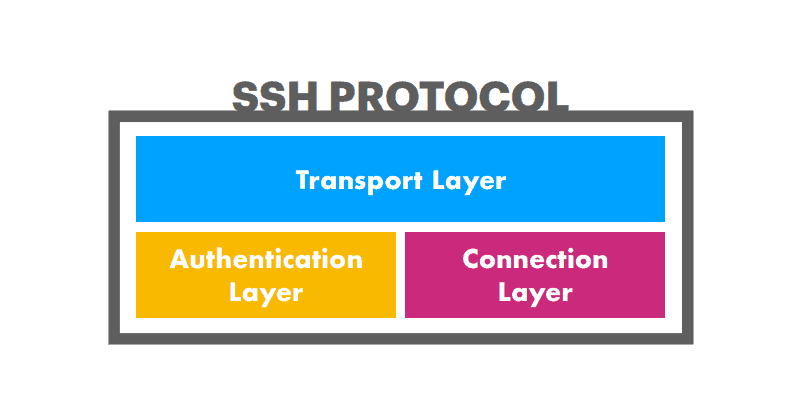
SSH consists of three distinct layers:
- The transport layer establishes safe and secure communication between a client and a server during and after authentication. It oversees data encryption, decryption, and integrity protection. Furthermore, it helps speed up data exchange by providing data compression and caching.
- The authentication layer communicates the supported authentication methods to the client. It also conducts the entire user authentication process.
- The connection layer manages the communication between the machines after the authentication succeeds. It handles the opening and closing of communication channels and allows multiple channels for multiple sessions.
What is SSH Used for?
SSH provides a layer of security for information transfer between machines. Some important use cases for SSH are:
- Remote access – SSH ensures encrypted remote connections for users and processes.
- File transfers – SFTP, a secure file transfer protocol managed by SSH, provides a safe way to manipulate files over a network.
- X11 Forwarding – Users can run server-hosted X applications from their client machines.
- Tunneling – This encapsulation technique provides secure data transfers. Tunneling is useful for accessing business-sensitive online materials from unsecured networks, as it can act as a handy VPN alternative.
- Network management – The SSH protocol manages network infrastructure and other parts of the system.
- Port Forwarding – By mapping a client’s port to the server’s remote ports, SSH helps secure other network protocols, such as TCP/IP.
Note: Learn how to forward ports with iptables or discover the differences between SFTP and SSH.
How Does SSH Work?
SSH is a client-server based protocol. This means the protocol allows a device requesting information or services (the client) to connect to another device (the server).
When a client connects to a server over SSH, the machine can be controlled like a local computer.
The server has a designated TCP port over which it monitors the network, waiting for clients to initialize the connection. Before a client connects and starts issuing SSH commands, it needs to pass the authentication process.
Establishing an SSH Connection
Run the following command on a client machine to initiate an SSH connection:
ssh [username]@[server_ip_or_hostname]When the server receives the requests, a session encryption negotiation begins.
Note: Read our guide on how to use SSH to connect to a remote server for a comprehensive list of steps.
Session Encryption Negotiation
Upon receiving a connection request, the server sends the client a set of supported encryption protocols. The server uses the public key as the authentication method.
The client compares the protocols to its own set. If there are matching protocols, the machines agree to use one to establish the connection.
The client compares the server’s public key to the stored private key stored in its system on the first connection attempt. If the keys match, the client and the server agree to use symmetric encryption to communicate during the SSH session. For this purpose, they communicate using an asymmetrically encrypted process that employs the Diffie-Hellman (DH) key exchange algorithm.
The DH algorithm enables machines to work together and securely create a cryptographic key over a public network. To generate a key, the machines perform the following steps:
- The machines agree on two numbers: a modulus and a base number. To prevent brute force key decryption, the chosen modulus is a prime number of at least 600 digits.
- The machines separately choose one number and apply it to the equation involving the two public numbers.
- The server and the client exchange the calculated values.
- Each machine now performs a calculation using the result received from the other.
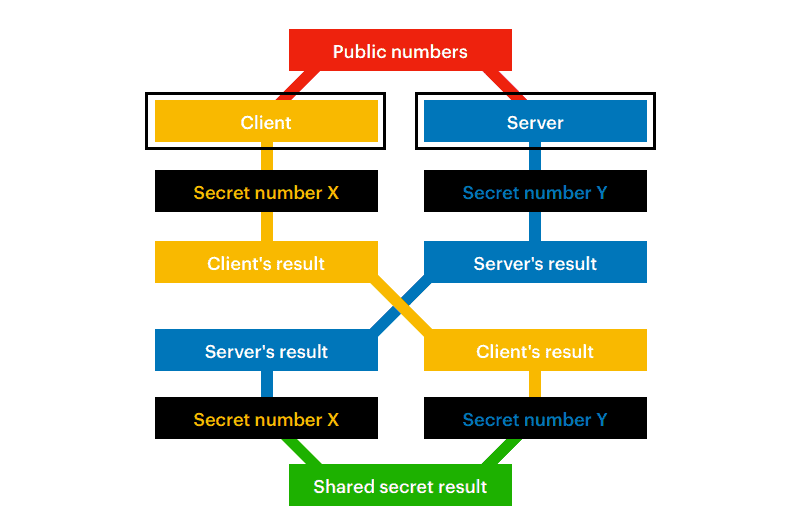
By performing the steps above, both machines calculate the same value, their secret key. Finally, the server then attempts to authenticate the user who requests access.
Note: Strong user authentication is one measure to apply to secure your SSH server. For more security tips, read our Linux SSH Security Best Practices article.
User Authentication
The two most common SSH user authentication methods used are passwords and SSH keys. The clients safely send encrypted passwords to the server. However, passwords are a risky authentication method because their strength depends on the user’s awareness of what makes a strong password.
Asymmetrically encrypted SSH public-private key pairs are a better option. Once the client decrypts the message, the server grants the client access to the system.
To generate an SSH key pair, type ssh-keygen in the terminal. As a result, the system generates and stores the keys.
For more information about this process, refer to How to Generate SSH Keys on Ubuntu (the process is essentially the same on all Linux distros and Mac OS).
Note: For the SSH key generation process in Windows, see How to Generate SSH Key in Windows 10.
Explaining SSH Encryption Technologies
SSH uses three data encryption types during the communication between the machines. These are:
- Symmetric encryption
- Asymmetric encryption
- Hashing.
Symmetric Encryption
Symmetric encryption generates a single key that two machines exchange. Then, the machines use the key for both encryption and decryption. This method is quick, it is not resource-intensive, and SSH uses it for each session.
Whenever the client and the server negotiate which algorithm to use for an SSH session, they always choose the first algorithm on the client’s list that the server supports.
Asymmetric Encryption
Data is asymmetrically encrypted when machines use two different but mathematically related keys, public and private, to perform the encryption. The client machine that participated in setting up the encryption can decrypt the information using the private key.
SSH uses temporal asymmetric keys to exchange symmetric keys, such as during the user authentication process.
Hashing
SSH uses hashing to validate if the data packets come from the source they appear to come from. Hashing algorithms used to produce hashes in SSH are Message Authentication Code (MAC) and Hashed Message Authentication Code (HMAC).
A hashing algorithm uses a data packet to create a unique hash string. The machine sending the packet always sends the packet together with the hash value.
The receiving machine knows the algorithm used to create the hash and can apply it to the data. The purpose is to see if the calculated hash value will be the same. If the obtained hash value differs from the sender’s hash, the data got corrupted during the transfer.
Note: Next you should learn is how to use SSHFS to mount remote file systems over SSH.
Conclusion
This article aimed to give you a better sense of the mechanisms behind SSH. Understanding how SSH works and why it is useful should help you decide if you want to use it in your personal or work environment.